Aerospace Defense Cyber Security Compliance Consulting Services - Our team will create an effective compliance program based on CMMC, NIST 800-171, NIST 800-53, and DoD directive.
Government contractors generally are familiar with cybersecurity FAR and DFARS clauses requirements, requiring contractors to implement cybersecurity programs to safeguard information systems. We can get you to comply faster with our experienced resources and security clearance experts.
Aerospace Cyber Security Consulting
CMMC-AB REGISTERED PROVIDER ORGANIZATION (RPO)
The Department of Defense (DoD) is developing a new framework for protecting government data and evaluating contractors’ cybersecurity compliance, known as the Cybersecurity Maturity Model Certification program (CMMC). Aerospace contractors and related firms have the challenge of recruiting and maintaining a full staff of security professionals with appropriate clearances and training them to handle the responsibilities of the defense sector. CyberSecOp provides some of the best security officers possible in a timely fashion, defense contractors need to turn to a security services provider who knows defense security and already has access to resources with clearance.
We provide strategic planning, security compliance services, and individual project support, taking the uniquely sensitive nature of your work into consideration. Among the extra products and services we can offer your Aerospace or Defense business are multi-factor authentication systems, password vaulting systems, advanced firewall, and content filtering services, secure email services, and encrypted mobility solutions. Comply with: DFAR, NIST 800 171/53, ITAR, CMMC, ISO 27001, AFI 33-210 Compliance, and other DOD Directives.
Cybersecurity CONSULTING for Aerospace
CMMC requirements apply to all DoD contractors and subcontractors. In other words, all contractors that perform under a contract that contains a CMMC requirement will be required to be certified under the program. DoD cybersecurity compliance, DFARS compliance, and NIST SP 800-171 compliance have become large-scale concerns for all Department of Defense (DoD) contractors since they were made effective in December 2017.
Companies engaged in the manufacture of products or involved in the use of technical data controlled by the U.S. Department of Defense (DOD) must comply with DFARS, including those applicable to export sales and shipments. CyberSecOp has extensive experience and knowledge of DOD regulations and requirements needed to support your business.
CyberSecOp will assist with Cybersecurity for Aerospace:
Deliver a unified view of cyber risk and vulnerabilities across your organization through risk-focused tools and procedures. Gauge the potential impact of risk-based decision-making on the mission. Reduce time spent obtaining DoD and other federal agency authorizations with reciprocal acceptance. Increase the likelihood of executing future projects on time and on budget by proactively building security into systems. Enhance efficiency through information assurance control inheritance and reuse.
DFARS NIST consulting Services with CyberSecOP
Aerospace Defense Security solutions
No need to worry CyberSecOp provides all the services needed to get you in compliance: Nexgen Firewall, Advanced Threat Endpoint Protection, Managed Patch Management, 24/7 Monitoring and Maintenance of your systems, Business Continuity Plan and Systems, Security and Incident Response Team.
Aerospace Vulnerability Assessments
CyberSecOp utilize a unified risk based approach based on NIST, OWASP and ISO to accomplish comprehensive vulnerability testing. This aid us in identifying gaps in multiple type of technology and environment to the CUI data, which is protected by DFAR.
Aerospace Penetration Testing
Our security team will simulate real-world attacks to assess the security control protecting external applications, systems, network, and mobile applications vulnerabilities.
Assess Risk to Aerospace Operations
Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or transmission of CUI.
Aerospace security Incident management & Reporting
If contractors experience a cyber incident that impacts CUI, then they must do the following:
Perform an analysis and gather evidence to determine if specific CUI was compromised on contractor computers or servers.
Rapidly report (within 72 hours) the discovery of the cyber incident. A medium-assurance certificate will be required to report the incident.
Preserve and protect OS images and other forensic evidence (e.g. packet captures, logs, etc.) for 90 days.
DFARS Gap ANALYSIS
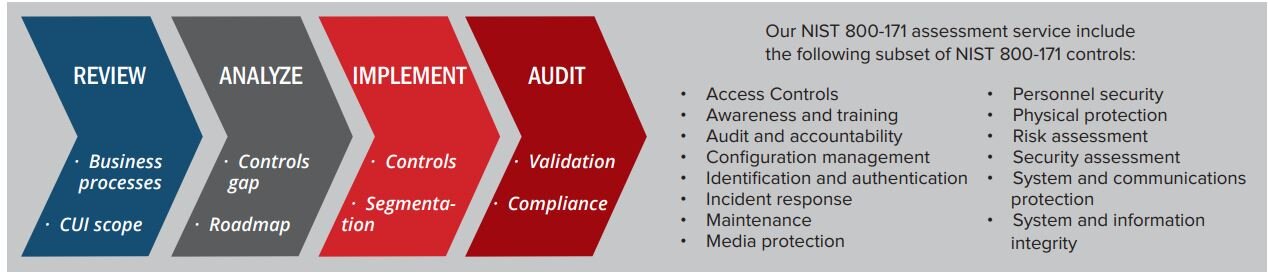
CyberSecOP’s security team will assess current compliance state and identify CUI exposure and potential liability. Findings will use to identify gaps in the security posture, verification of current policies and procedures to safeguard CUI, and a detailed roadmap and recommended measures for NIST 800-171 compliance.
Review 24/7 monitoring and maintenance of your systems
Review business continuity plan in times of disaster
Aerospace IT Infrastructure
Assessments infrastructure control, to identify gaps in relation to overall security of system and in compliance with DFAR and NIST 800-171, Below are some of the more commonly practiced NIST-800-171 Special Publications that CyberSecOp Secure has experience in assisting with implementation, design, authorization and configuration:
Aerospace & DFARS
Depending on the nature of your DoD contract, you will be expected to self-certify compliance with one or more of the following clauses. Our specialists are here to help.
DFARS 252.204-7008: Compliance with Safeguarding Covered Defense Information Controls
DFARS 252.204-7009: Limitations on the Use or Disclosure of Third-Party Contractor Reported Cyber Incident Information
DFARS 252.204-7012: Safeguarding Covered Defense Information and Cyber Incident Reporting
Aerospace Implement System Security Plans
Develop, document, periodically update, and implement system security plans for organizational information systems that describe the security requirements in place or planned for the systems.
3.8 Media Protection
3.9 Personnel Security
3.10 Physical Protection
3.11 Risk Assessment
3.12 Security Assessment
3.13 Systems and Communications
3.14 Systems and Information Integrity
3.1 Access Control
3.2 Awareness and Training
3.3 Audit and Accountability
3.4 Configuration Management
3.5 Identification and Authentication
3.6 Incident Response
3.7 Maintenance
Aerospace NIST Security Program Overview
Risk Categorization: Organizations must categorize their information and information systems in order of risk to ensure that sensitive information and the systems that use it are given the highest level of security.
System Security Plan: DFARS NIST 800 requires agencies to create a security plan which is regularly maintained and kept up to date. The plan should cover things like the security controls implemented within the organization, security policies, and a timetable for the introduction of further controls.
Security Controls: DFARS NIST 800 outlines an extensive catalog of suggested security controls for NIST compliance. NIST does not require an agency to implement every single control; instead, they are instructed to implement the controls that are relevant to their organization and systems. Once the appropriate controls are selected and the security requirements have been satisfied, the organizations must document the selected controls in their system security plan.
Risk Assessments: Risk assessments are a key element of DFARS NIST’s information security requirements. NIST 800 offers some guidance on how agencies should conduct risk assessments. According to the NIST guidelines, risk assessments should be three-tiered to identify security risks at the organizational level, the business process level, and the information system level.
Certification and Accreditation: NIST requires program officials and agency heads to conduct annual security reviews to ensure risks are kept to a minimum level. Agencies can achieve NIST Certification and Accreditation (C&A) through a four-phased process which includes initiation and planning, certification, accreditation, and continuous monitoring.