SECURITY PROGRAM DEVELOPMENT SERVICES
Security Program Development: Security Policies and Procedures Development. We take your security to the next level by introducing policies and controls. Managed Security Program as a Service you can depend on to ensure your business is secure and compliant.
Security Program Development
CyberSecOp Managed Security Program as a Service digitally transformation risks by delivering a holistic mature cyber security program. Our VCISO security program team has developed and implemented comprehensive information security programs in every sector.
To merely respond is costly. You lose data, valuable time, and business, and the organization loses clients in most cases. Having the right team to develop your security program is essential; you can count on our experienced security consulting group to implement a complete security program, including a security framework, risk management, security operation, incident response, and governance service. Our cyber security program provides an average 210% ROI achieved by reducing resource and technology costs and preventing attacks on pre-execution services.
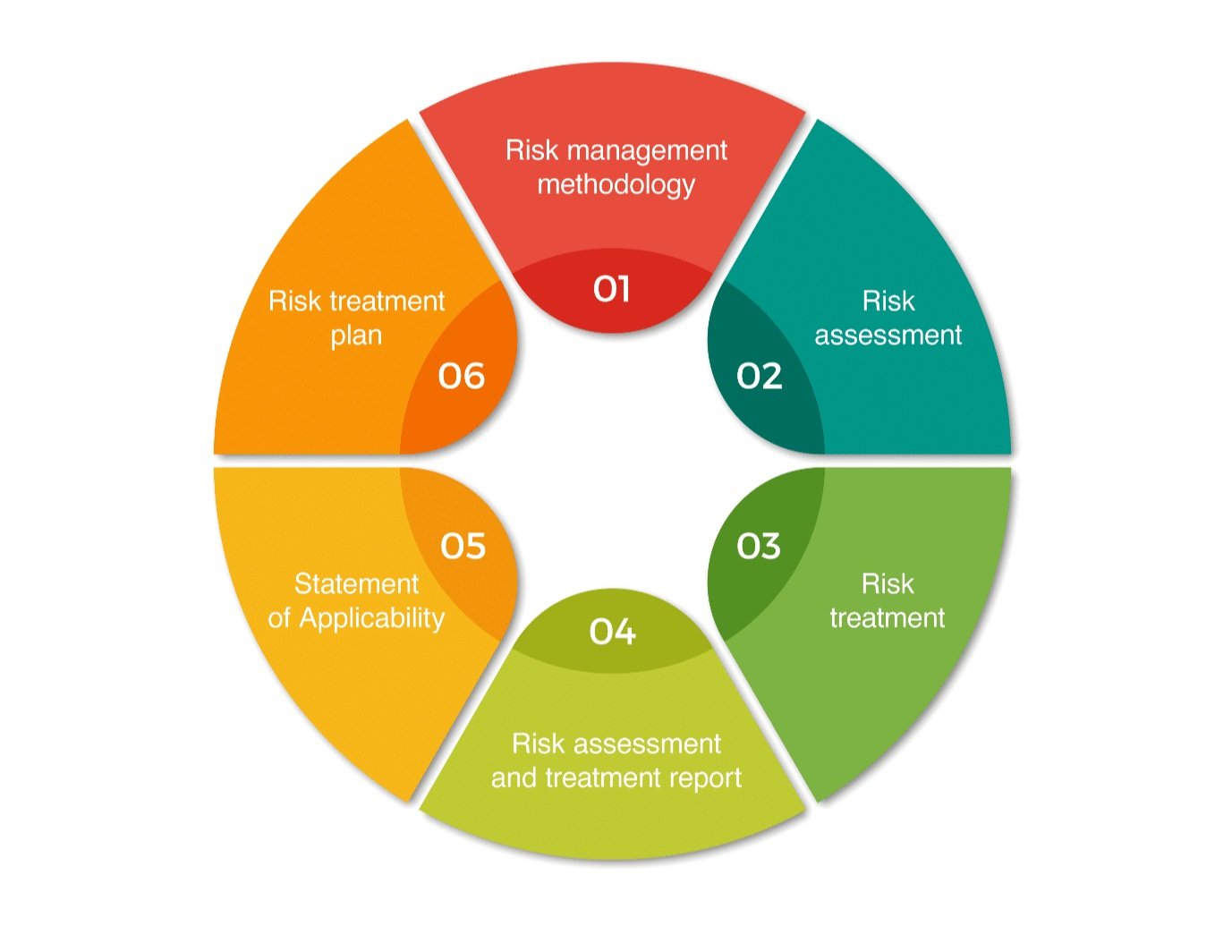
Our security programs include Cyber Security Risk Management, Third-Party Risk Management, Vulnerability Management, Penetration Testing, Employee Security Training Awareness, Data Privacy Program, Security Program Development, Business Continuity Plan, Incident Response, and Forensics Services.
Cyber and Information Security Program
Cybersecurity program consulting solutions tailored to each individual client requirements delivering cyber risk assessment, information security, compliance and privacy services to leading enterprises.
Why CyberSecOp Cyber Security Program?
CyberSecOp offers a variety of security programs, each suited to your company's needs, to assist you in proactively identifying security vulnerabilities and fine-tuning your security approach. To continue growing your software and improving its defenses, we advocate a regular cadence of security assessments and testing.
Compliance Security Program
Regulatory Compliance Services
Virtual CISO (vCISO)
Risk Assessment and Risk Management
Program Design & Progam Management
Develop Policies and Procedures
Security Strategy and Governance
Security Incident Response Planning
Security Architecture Review
Vendor Risk Management Program
Vulnerability Management Program
Dark Web Monitoring
Security Awareness Training
C-Level Compliance Reporting
Cyber Security Program
Regulatory & Cyber Compliance
Virtual CISO (vCISO)
Security Programs Maturity Assessment
Managed Vulnerability Service
Security Policy Review
Security Incident Response Planning
Security Architecture Review
Vendor Risk Management Program
Vulnerability Management Program
Phishing and Security Awareness Training
External Penetration Test
Threat Advisories
Executive Briefing
Red Team Exercise
Cyber Security Operations
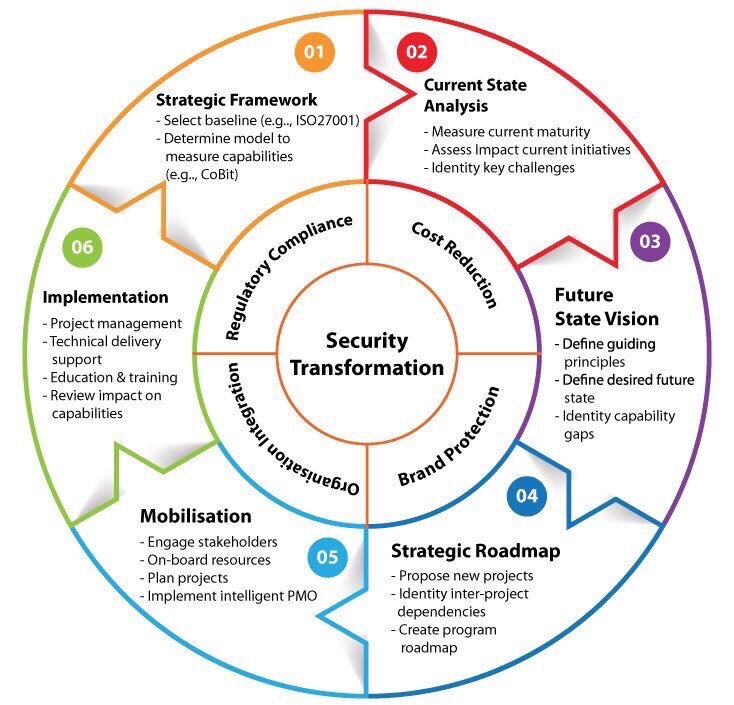
Having a security program will help you ensure the confidentiality, integrity, and availability of your client and customer information and your organization's essential data. Our Cyber Security Operations Consulting Firm, Cybersecurity Program Maturity, and Strategy Advisement is focused on helping businesses with a customized methodology refined over thousands of global engagements to help analyze an organization’s current security maturity levels and roadmap according to their unique environment and industry. This comprehensive methodology includes detailed phases to support organizations on their cybersecurity strategy development journey.
Security Program Approach
Gathering information to understand the perception of security maturity levels, how security engages with the business, the organization’s strategy overall and the business direction
Analyzing the current state of cybersecurity maturity
Defining a security capability maturity target, with both business and security staff, to define exactly where they need to set their security benchmark
Developing a road map against the target
Elevate your organization security program posture
CyberSecOp provides a variety of comprehensive security programs suited to your company's needs to assist you in detecting security weaknesses and improving your security strategy. Our cyber security consulting program includes Cyber Security Risk Management, Third-Party Risk Management, Vulnerability Management, Penetration Testing, Employee Security Training and Awareness, Data Privacy Program Development, Security Program Development, Business Continuity Plan, Incident Response, and Forensics Services, is strongly recommended.
IT Security Program - Implementation of success factors and continued optimization
We provide complete Cyber Security Program Management
Comprehensive Cyber Security Assessment Services
Security Program Governance
Build Your Strategy First for your Program: Your security program strategy represents the overall direction for security in your organization’s public demand for security. As a result, it needs to be built before any other components of your security program.
Security Program Development Tool
Security Program Development Considerations
Security Program Metrics
Regulatory Review
Managed Security Program as a Service
Your organization can focus on growing, we will focus on Information Security Program Applying appropriate administrative, technical, and physical safeguards.
Security Program Frameworks
The cyber security program is the full, multi-faceted security strategy and governance that protects your organization's sensitive data and capabilities.
Sarbanes-Oxley (SOX) for publicly traded companies and those planning to go public
PCI DSS for financial entities and services that process credit card data
HIPAA/HITECH for hospitals, insurance providers, and other organizations collecting personal health information (PHI)
ISO for companies aiming to improve their security and quality management controls
Privacy Shield, which replaces the US-EU Safe Harbor, for organizations that collect and process data between the U.S. and European Union
NIST for government agencies, large enterprises, and any organization looking to minimize their cybersecurity risk
SOC 1 and SOC 2, SOC 1 report is designed to address internal controls over financial reporting while a SOC 2 report addresses a service organization's controls relevant to their operations and compliance.
An effective cyber security program includes a myriad of policies and procedures, encompassing risk management, incident management, third-party management, regulatory and audit compliance, as well as disaster recovery and business continuity planning.
Elevate your organization security program posture
CyberSecOp provides a variety of comprehensive security programs suited to your company's needs to assist you in detecting security weaknesses and improving your security strategy. Our cyber security consulting program includes Cyber Security Risk Management, Third-Party Risk Management, Vulnerability Management, Penetration Testing, Employee Security Training and Awareness, Data Privacy Program Development, Security Program Development, Business Continuity Plan, Incident Response, and Forensics Services, is strongly recommended.
IT Security Program - Implementation of success factors and continued optimization
We provide complete Cyber Security Program Management
Comprehensive Cyber Security Assessment Services
Security Program Governance
Build Your Strategy First for your Program: Your security program strategy represents the overall direction for security in your organization’s public demand for security. As a result, it needs to be built before any other components of your security program.
Security Program Development Tool
Security Program Development Considerations
Security Program Metrics
Regulatory Review
What is a Cyber Security Program?
A cyber security program is a documented set of your organization's information security policies, procedures, guidelines, and standards. Your security program should provide a roadmap for effective security management practices and controls.