CYBER SECURITY OPERATIONS CENTER SERVICES
Our cyber security operations center (CSOC) services help to keep information security systems under constant surveillance. The CyberSecOp team will use advanced technology to continuously monitor and analyze your organization's security posture, ensuring transparency and productivity in a secure data flow environment.
Cyber Security Operations Center (CSOC)
Security Operations Center (SOC) & Threat Intelligence services
CyberSecOp Cyber Security Operations Center (CSOC) is a centralized unit that manages an organization's security posture. Our CSOC services typically include monitoring and defending against cyber threats, responding to security incidents, and implementing security policies and controls. Some specific activities that a CSOC might perform include:
Intrusion detection and prevention: Monitoring network traffic for signs of cyber attacks and taking action to block or mitigate them.
Vulnerability management: Scanning systems and networks for vulnerabilities and taking steps to fix them before they can be exploited.
Security incident response: Coordinating the organization's response to security incidents, including identifying the cause of the incident, containing it, and recovering from it.
Security intelligence: Gathering and analyzing information about cyber threats and vulnerabilities to inform the organization's security posture.
Security policy and compliance: Developing and enforcing security policies and procedures and ensuring compliance with relevant laws and regulations.
Cybersecurity training and awareness: Providing training to employees on cybersecurity best practices and helping to increase awareness of cyber threats.
Security Operations Center (SOC) Services
24x7x365 Managed Cybersecurity SOC
We provide the cyber security expertise you need with SOC-as-a-Service and managed security services for cloud environments, endpoints, and networks.
SOC as a Service Features and Benefits
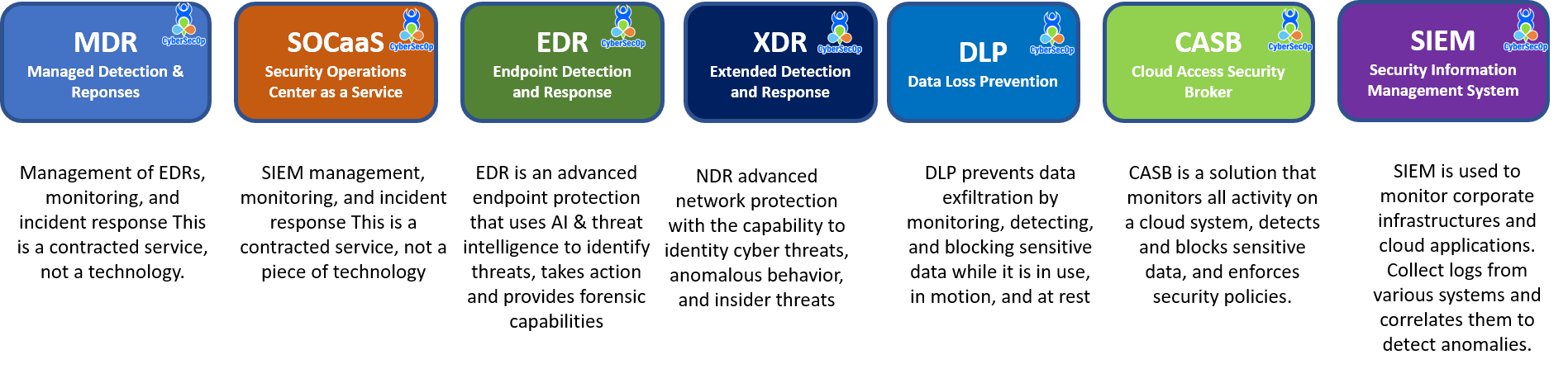
Our Security Operations Center (SOC) as a Service managed security service provides an organization with the ability to outsource the management and operation of its security operations center to a third-party service provider. The provider is typically responsible for managing the organization's security infrastructure, which includes firewalls, intrusion detection and prevention systems, and security information and event management (SIEM) systems, as well as providing 24/7 monitoring and incident response services.
SOC as a Service allows organizations to tap into the expertise and resources of a specialized security provider without having to build and maintain their own security operations center. It can also assist organizations in lowering the risk of security breaches while meeting compliance requirements.
Managed SOC Services
CyberSecOps security operations center (SOC) and MDR provides you software, platform, technologies and the expert staff to monitor, manage and threat hunt to let you focus on your business goals.
What Cyber Security Operations Services
Cybersecurity operations services help organizations protect their networks, systems, and data from cyber threats. These services can include:
Security monitoring: This involves continuously monitoring an organization's networks and systems for signs of potential threats or vulnerabilities.
Incident response: This involves identifying and responding to cybersecurity incidents when they occur, such as by containing the threat, restoring affected systems, and conducting a forensic analysis to determine the cause of the incident.
Vulnerability management: This involves identifying and mitigating vulnerabilities in an organization's systems and networks, such as by patching software or updating security configurations.
Compliance management: This involves helping organizations meet regulatory requirements and industry standards related to cybersecurity.
Security training and awareness: This involves educating employees about cybersecurity best practices and helping them understand their role in protecting the organization's assets.
Many cybersecurity operations services providers offer various services to help organizations protect their assets from cyber threats.
Security Operations Center Tools Used
These are just a few examples of the many tools used in cybersecurity operations.
Intrusion detection and prevention systems (IDPS): These are tools that monitor an organization's networks and systems for signs of cyber attacks or attempts to access unauthorized resources and take action to prevent these attacks or access attempts.
Security information and event management (SIEM) systems: These are tools that collect and analyze security-related data from various sources, such as logs generated by servers and security devices, to identify potential threats and provide alerts to security personnel.
Vulnerability scanners: These are tools that scan an organization's systems and networks to identify vulnerabilities that attackers could exploit.
Firewalls: These are tools that monitor and control incoming and outgoing network traffic based on predetermined security rules.
Encryption tools: These are tools that encrypt data to protect it from unauthorized access.
Identity and access management (IAM) systems: These are tools that manage and control access to an organization's systems and resources based on users' roles and permissions
Data Loss Prevention (DLP) is a security measure that helps organizations prevent sensitive data from being lost, stolen, or accessed by unauthorized individuals. DLP systems monitor an organization's networks and systems for the transmission or storage of sensitive data and take action to prevent unauthorized access or transfers of that data.
A SOC is a centralized unit responsible for monitoring and analyzing the organization's security posture and responding to security incidents. The SOC collects data from a wide range of sources, including networks, devices, and appliances, and uses this data to identify potential threats and vulnerabilities. When a potential threat is identified, the SOC analyzes the situation. It determines the appropriate action, including activating incident response protocols, alerting relevant stakeholders, and taking steps to prevent or mitigate the threat. The SOC also plays a crucial role in coordinating the organization's response to security incidents, ensuring that the appropriate resources are mobilized and that the incident is resolved in a timely and effective manner.