CYBER SUPPLY CHAIN RISK MANAGEMENT SERVICES
Cyber Supply Chain Risk Management (C-SCRM) is identifying, assessing, and mitigating the risks associated with the distributed and interconnected nature of IT/OT product and service supply chains.
Together with all of our partners to identify and address potential supply chain risks, we can provide you with the technology and information you need while upholding the highest standards of cyber security. Because they are knowledgeable and experienced in managing the risk associated with the cyber supply chain, our technology team consistently works to keep our and your data secure.
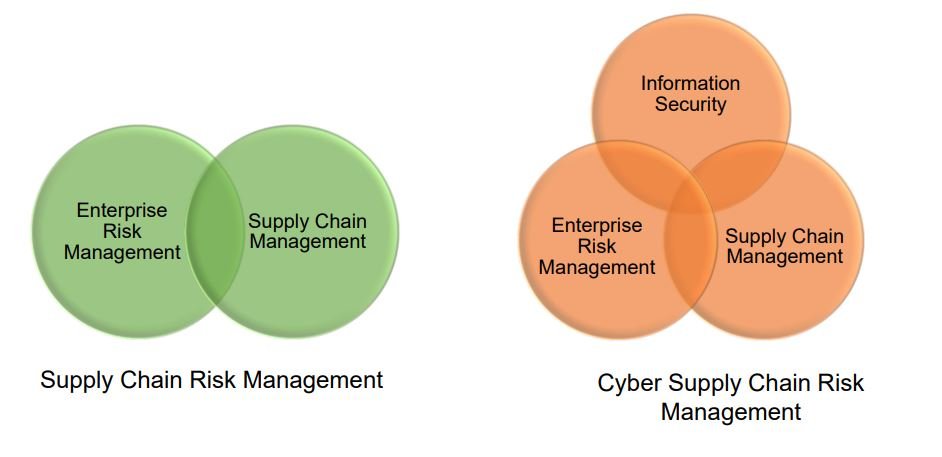
Cyber Security Supply Chain Risk Management
Vendors and third-party partners assist your business in growing and remaining competitive. However, they also expose your organization to cyber risk. A few examples are the SolarWinds hack and the Target breach; the supply chain can contain weak links, making it a favorite attack vector for hackers.
This is because malicious attackers look for the weakest link in an organization's security posture. This is often found in your company's interconnected supply chain. When dealing with potentially hundreds of vendors, some of whom handle sensitive data, third-party and supply chain risk management can be overwhelming, but it is necessary to manage.
Addressing these cyberattacks requires a layered defense in which third-party integrations are audited, endpoints are monitored for post-compromise actions, and an Incident Response plan that considers supply chain risks is put in place to minimize impact.
Cyber Supply Chain Risk Management
Suppliers and third-party partners are routinely assessed using audits, test results, or other forms of evaluations to confirm they are meeting their contractual obligation.
Defining the Audit and Verification Process
Identify Controls to be Verified and Method of Verification
Conducting Supplier Audits
Maintaining the Verification Process
Eliminating Gaps in Contractual Compliance
Supply Chain Risk Assessment Services
With the Supply Chain Risk Assessment, you can measure your organization’s strategy, capabilities, and controls associated with your supply chain. Here is what you get:
+ Cyber Supply Chain Risk Management Services
We have extensive experience in the cyber security field and can help you build or optimize your cyber supply chain risk management. We assist you in understanding your current risk landscape, measuring your risks, defining your supply chain risk management strategy, and implementing the necessary measures.
On the basis of your business processes, we assist you in defining and managing relevant criteria that enable suppliers to meet your company's cyber security goals. Simultaneously, we assist you in assessing and managing your overall cyber security risk.
+ Red Team Attack Simulation Services
CyberSecOp Red Team Advanced Penetration Testing starts with a clear understanding of your vulnerabilities and risk; penetration testing plays an essential role. We have performed over 100 red team exercises on both corporate office and industrial plant locations, and we have the resources, methodology, and experience to perform these tests in a safe manner that does not impose any operational risk to our clients
With our red team, we will perform Application Penetration Testing, Network Penetration Testing, Vulnerability Testing, Phishing Testing, and Social Engineering to find the weak spots in your critical assets/employees and recommend corrective action before attackers exploit them, sabotage your business or steal your confidential data.
+ Network Penetration Testing Services – External or Internal
Red Teaming Penetration testing of internal networks An internal network penetration test is carried out to find out what an attacker could do if they had full access to the network. A test of an internal network's vulnerability can simulate insider threats, such as employees behaving maliciously either intentionally or unintentionally.
Red Team External Network Penetration Testing An external network pen test is intended to evaluate how well perimeter security measures deter and detect attacks as well as find vulnerabilities in internet-facing assets like web, mail, and FTP servers.
Red Team Wireless Network Penetration Testing Services Our wireless assessment methodology, which simulates actual attacks to provide a point-in-time assessment of vulnerabilities and threats to your wireless network infrastructure, is built on the Open Source Security Testing Methodology Manual (OSSTMM) and the Penetration Testing Execution Standard (PTES). Red teaming simulates a real-life attack to measure your risk.
+ Web Application Penetration Testing Services
CyberSecOp leads the industry in web application penetration testing, identifying vulnerabilities in a range of programming languages and environments. From webapps in highly scalable AWS environments to legacy apps in traditional infrastructure, out security experts have helped secure data across the world.
With dozens of zero-day vulnerabilities disclosed and our research circulating on national news outlets, we consistently prove our commitment to top-notch security testing.The architecture, design, and configuration of web applications are evaluated during a web application penetration test, a type of ethical hacking engagement. Cybersecurity risks that could result in unauthorized access and/or data exposure are assessed.
+ Mobile Application Penetration Testing Services
CyberSecOp has experience with multiple security frameworks, and mobile app security standards. Successful mobile app pen testing begins with decades of skills, exemplary customer service, flexible scheduling, and lightning-fast turnaround time. Our team has extensive knowledge of mobile device testing sets us a from other penetration testing services providers.
The CyberSecOp Red Team is a global team of hackers hired to break into organizations and discover potentially dangerous vulnerabilities that attackers may exploit for personal gain.
+ IoT Testing Services
A team of IoT-skilled testers, a strong IoT testing infrastructure (labs, simulators, test racks, etc.), and CyberSecOp's experience in IoT app Testing as a Service (TaaS) support real-time testing of Big Data, Compatibility, IoT Security, Performance, Pilot, Regulatory, Reliability, Upgrade, and smart devices in a dynamic environment. The offensive red team security services provided by the team, which include penetration testing, vulnerability management, and adversary simulation, can assist in identifying, prioritizing, and correcting security flaws across your entire digital and physical ecosystem.
+ Social Engineering Penetration Testing Services
Penetration testing for social engineering focuses on people, processes, and the vulnerabilities connected to them. The goal of a social engineering attack typically entails persuading individuals to reveal sensitive information or engage in beneficial behavior for the attacker, preferably without their knowledge. Information security programs frequently need to perform regular penetration tests to simulate the threat of social engineering attacks. Benefits of social engineering tests include:
Identify vulnerabilities relating to attacks that leverage people and process. Understand the likely impact of an attacker that uses social engineering. Gain insight into what people and process defenses are currently working well. Get assurance that includes consideration of real-world threats such as phishing
+ Ransomware Attack Simulation Services
CyberSecOp Ransomware Attack Simulation Red Team Service is an excellent service and platform for simulating a breach and attack. To provide red team security services, multiple tools and red team security experts use a combination of MITRE ATT&CK playbooks and ransomware to directly correspond to TTPs seen in actual attack scenarios. Our ransomware simulation services will find out how vulnerable your network is to common ransomware and cryptomining attacks.
To defeat modern ransomware attacks, you must first find and stop the malicious behaviors that precede the ransomware. Our ransomware red team investigates every major strain of ransomware in order to continuously improve our multi-layer prevention and behavioral threat detection approach.
Cyber Supply Chain Risk Management (C-SCRM) Best Practices
Prevent vendor cybersecurity gaps from disrupting business operations and impacting your customers. Start by evaluating your cybersecurity supply chain risk management strategy, capabilities, and controls.
Understand Profiled, Inherent, and Residual Vendor Risk
Understanding different types of vendor risk can enable you to make data-based decisions on how to apply vendor risk questionnaires, as well as to accurately compare vendors based on measurable risk. To put it simply:
Profiled Risk: Relates to risk based on the service that the contractor is performing. An MSP that has access to your IT environment likely poses far more risk than a plumbing company.
Inherent Risk: Inherent risk is the amount of risk a company poses prior to implementing security controls required by your organization.
This C-SCRM product and services assurance questionnaire addresses the following areas of risk:
Acknowledgment. Management and employees need to feel empowered to pass on bad news and lessons from mistakes. This openness fosters an environment where it is okay to voice and deal with issues. Culturally, it is critical that the organization not get discouraged or point fingers when a risky event occurs and instead work harmoniously towards a rapid resolution.
Transparency. Leaders must clearly define and communicate an organization’s risk tolerance. Risk mitigation often has an associated incremental cost, and so it is important to align on which risks need to be mitigated and which can be borne by the organization. An organization’s culture should also allow for warning signs of both internal and external threats to be openly shared.
Responsiveness. Employees need to be empowered to perceive and react rapidly to external change. This can be enabled by creating an ownership environment, where members feel responsible for the outcome of actions and decisions.
Respect. Employees’ risk appetites should be aligned with organizations so that individuals or groups do not take risks or actions that benefit themselves but harm the broader organization.
Risk Identification. The only way to address risk is to make sure you’re identifying it in the first place. The first phase of the risk management lifecycle is to establish a risk profile and then enact active monitoring to keep it up to date.
Risk Assessment, Understand what impact a risk event could have on your business. Be aware of those partners who have a significant impact on sales, margins, or profit.
Risk Mitigation. Define both preventive action plans and reactive action plans. These provide the basis for addressing risk using appropriate measures to secure supply and protect the brand.
Supply Chain Findings Report
Leveraging our proprietary vendor due diligence framework, CyberSecOp assesses your cyber risks, documents our findings, and provides recommendations to help you guide your supply chain vendors to achieve a desirable risk posture.
What is Supply Chain Risk Management?
Supply-chain risk management is part of the wider process of supply-chain management, which involves managing the entire production flow of your business. It’s the process of identifying risks in your supply chain, assessing the likelihood and severity of these risks, and taking strategic steps to eliminate or control them.
Supply-chain risk-management strategies should be worked into your business’ policies, procedures, and operations — and those of your suppliers. This can help you ensure risks are controlled, and that compliance is maintained throughout your entire supply chain.