CyberSecOp: CyberSec Consulting Services
professional Cyber Security & Consulting service
CyberSecOp: CyberSec Consulting services helps companies build their cybersecurity strategy & discover threats and risks, before the can cause hard to your business. Our CyberSec consultants understand that cyber security is at the core of every business no matter if you’re a small/medium size business (SMB) or a large enterprises.
CyberSecOp Security is a leading provider, we understand that cyber crime is at all time high and they are setting their sight on small to midsize businesses. CyberSecOp: CyberSec Consulting services offers end-to-end cybersecurity services, including advanced cyber defense, applied cybersecurity solutions and managed security operations. We bring security innovation, coupled with global scale and a worldwide delivery capability through our network of Advanced Technology and Intelligent Operations centers. Helped by our team of highly skilled professionals, we enable clients to innovate safely, build cyber resilience and grow with confidence.
Cybersec risk mitigation & COMPLIANCE Services
CyberSecOp: CyberSec Consulting services automate your cyber security and compliance, with CyberSecOp all complete security management and compliance solutions to enforce protection for your devices, users, networks, and applications.
CyberSec Consulting: Making Cyber Security a Priority
Mitigating the threat of a cyber attack is on the top of every business’ strategic list, and if it is not well there will be multiple breaches in your future, if one isn’t happening right now, without you knowing. Without the right team it can be difficult to pinpoint hidden vulnerabilities, create the right action plan, and safeguard data assets while complying with new laws. It takes an experienced CyberSec consulting company to identify potential cyber security threats and create a comprehensive road map plan to protect your business assets.
Confidentiality — ensuring sensitive data is only accessible to those people who actually need it, and are permitted to access according to organizational policies, while blocking access to others.
Integrity — making sure data and systems are not modified due to actions by threat actors, or accidental modification. Measures should be taken to prevent corruption or loss of sensitive data, and to speedily recover from such an event if it occurs.
Availability — ensuring that data remains available and useful for its end-users, and that this access is not hindered by system malfunction, cyber attacks, or even security measures themselves.
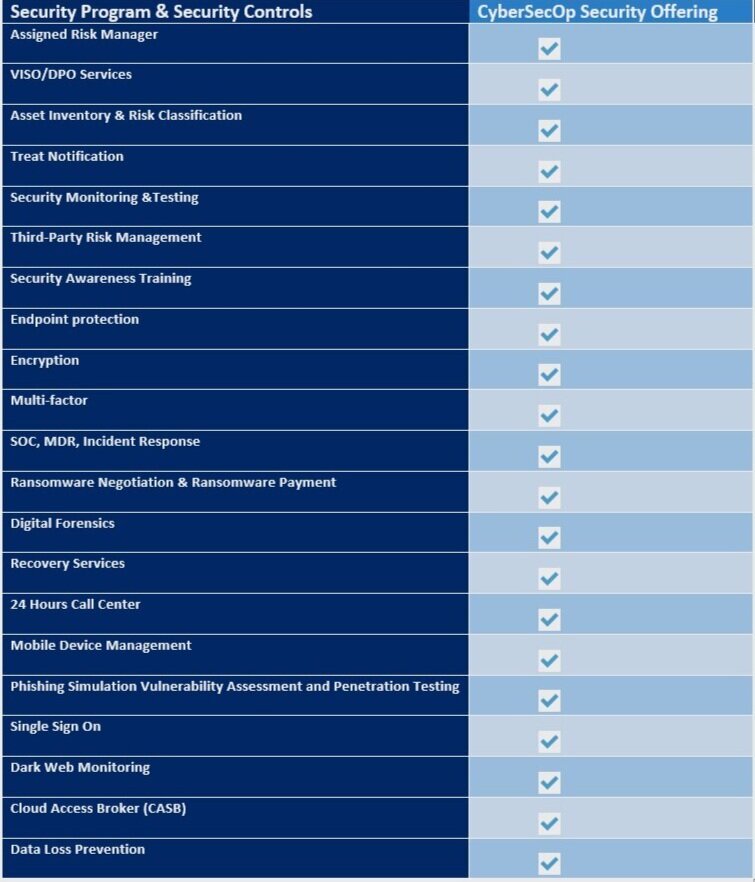
Benefit of CyberSecOp: CyberSec Services
CyberSecOp: CyberSec Consulting mission is to foster the building of an wide cybersecurity system and to create a dedicated, collaborative platform allowing our client to share there pain point and resolution. CyberSec specialist in the securing technology and protecting digital assets by defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks.
Security breaches and threats can affect
Communication — phone calls, emails, text messages, and messaging apps can all be used for cyberattacks
Finance — naturally, financial institutions are a primary target for attackers, and any organization processing or dealing with bank or credit card information are at risk
Governments — government institutions are commonly targeted by cybercriminals, who may be after private citizen information or confidential public data
Transportation — connected cars, traffic control systems and smart road infrastructure are all at risk of cyber threats
Healthcare — anything from medical records at a local clinic to critical care systems at a national hospital are vulnerable to attack
Education — educational institutions, their confidential research data, and information they hold about students or staff, are at risk of attack