CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
What are Cyber Security Services?
What is cyber security?
Cybersecurity refers to the practices and technologies used to protect computers, networks, and devices from cyber-attacks and threats. Cybersecurity is critical because it helps to ensure the confidentiality, integrity, and availability of information and systems. Cyber attacks can come in many forms, such as malware, ransomware, phishing, and Denial of Service (DoS) attacks. They can have serious consequences, including the theft of sensitive data, the disruption of business operations, and the loss of money. To protect against these threats, organizations, and individuals can use a variety of cybersecurity measures, such as firewalls, antivirus software, and strong passwords. It is also essential to educate users about how to recognize and avoid cyber threats and to keep software and systems up to date with the latest security patches.
What are Cyber Security Services?
There are many different types of cybersecurity services that organizations and individuals can use to protect themselves against cyber threats. Some examples of cybersecurity services include:
Managed security services: These services provide ongoing monitoring and protection of an organization's networks and systems by a team of cybersecurity experts.
Network security: This type of service protects an organization's networks from external threats, such as hackers and malware.
Cloud security: This service helps to secure an organization's data and applications that are hosted in the cloud.
Email security: This service helps to protect against threats that are transmitted through email, such as phishing attacks and spam.
Endpoint security: This service helps to protect the devices that are used to access an organization's networks and systems, such as laptops and smartphones.
Web security: This service helps to protect an organization's website and web-based applications from threats such as malware and hacking.
Identity and access management (IAM): This service helps to ensure that only authorized users have access to an organization's systems and data.
Compliance and risk management: This service helps organizations to comply with relevant laws and regulations and to manage their cybersecurity risks.
Incident response: This service helps organizations to respond to and recover from cybersecurity incidents, such as data breaches and cyber attacks.
What is security compliance?
Security compliance refers to the process of following rules, guidelines, and standards that are designed to protect an organization's information and systems from cyber threats. These rules and standards may be mandated by laws and regulations, or they may be voluntary industry standards. Some examples of security compliance frameworks and standards include:
The Payment Card Industry Data Security Standard (PCI DSS): This standard applies to organizations that accept, process, or store credit card payments and is designed to protect against the theft of cardholder data.
The Health Insurance Portability and Accountability Act (HIPAA): This law applies to organizations in the healthcare industry and sets standards for protecting patient health information.
The General Data Protection Regulation (GDPR): This law applies to organizations that process the personal data of individuals in the European Union (EU) and sets standards for data protection and privacy.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework: This framework guides organizations on how to manage and reduce their cybersecurity risks.
The International Organization for Standardization (ISO) 27001: This standard provides a framework for an organization's information security management system (ISMS).
Following security compliance standards can help organizations to protect their information and systems from cyber threats and avoid fines and other penalties for non-compliance. It is important for organizations to assess their compliance with relevant standards regularly and to implement measures to address any gaps.
Managed security service providers (MSSPs)
Managed security service providers (MSSPs) are companies that offer a range of cybersecurity services to organizations on a subscription basis. These services may include ongoing monitoring and protection of an organization's networks and systems, incident response, and compliance assistance. MSSPs can help organizations to improve their cybersecurity posture and reduce the risk of cyber attacks in several ways:
Expertise: MSSPs typically have teams of cybersecurity experts with the knowledge and experience to identify and mitigate potential threats.
Continuous monitoring: MSSPs can provide continuous monitoring of an organization's networks and systems, which can help to identify and respond to threats in real time.
Time and cost savings: Outsourcing cybersecurity to an MSSP can save an organization time and resources that would otherwise be spent on in-house cybersecurity efforts.
Compliance assistance: MSSPs can help organizations to ensure compliance with relevant security standards and regulations.
By working with an MSSP, organizations can benefit from the expertise and resources of a dedicated cybersecurity team, which can help to improve their overall security posture and reduce the risk of cyber attacks.
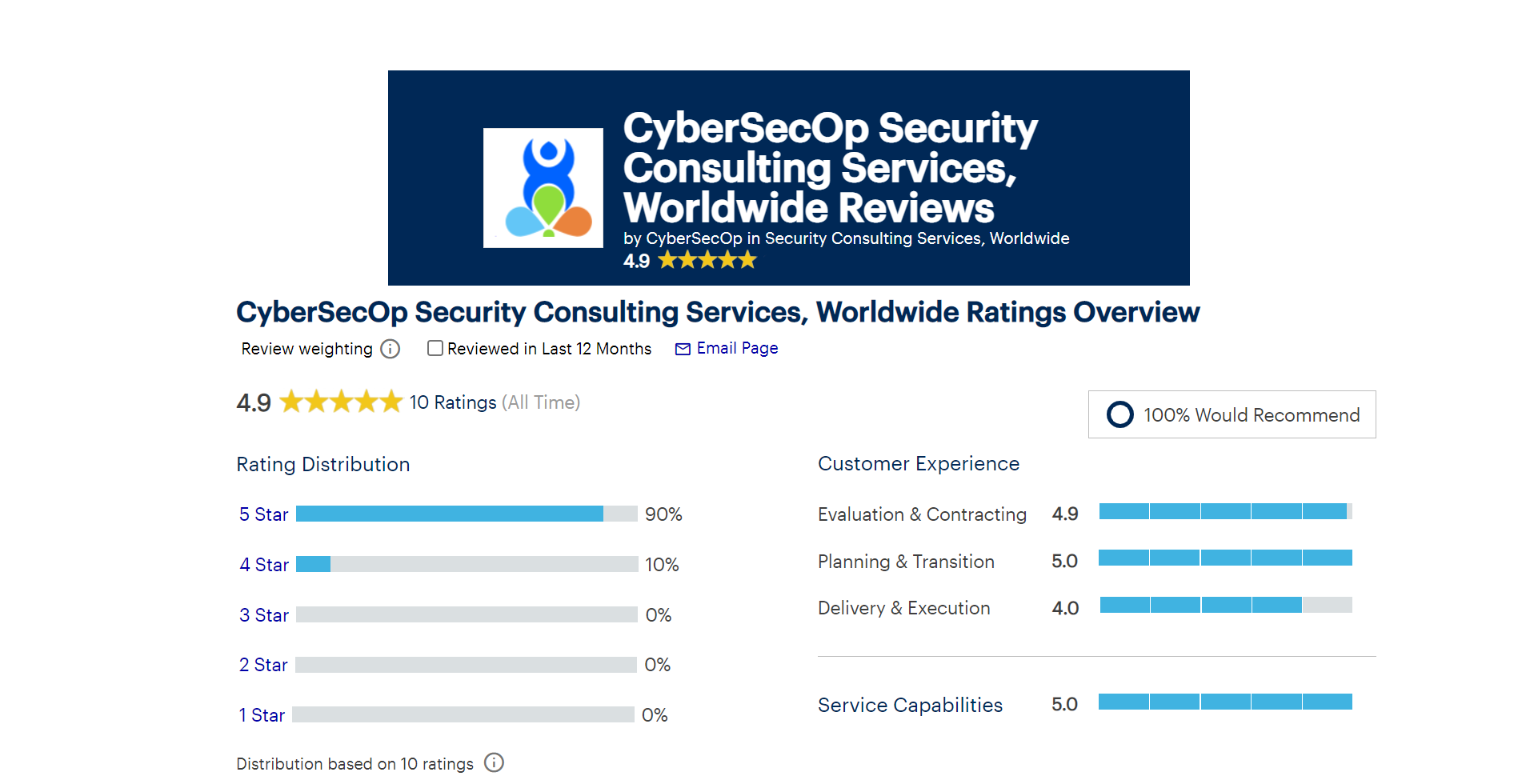
Gartner Recognizes CyberSecOp - Ranked 2nd for Security Consulting Worldwide.
CyberSecOp receives the highest overall score on Gartner Peer Insights for Security Consulting Services, Worldwide in 2022.
June 8, 2022 - CyberSecOp today announced that its Security Consulting Services received a 4.9 out of 5 overall rating from Gartner Peer Insights, placing CyberSecOp in the top two on Gartner’s Security Consulting Services Worldwide category.
"Peer reviews are extremely valuable for evaluating any purchase decision," said Josh Bauer, Executive Director at Loxo Oncology/Lilly. “CyberSecOp appears to actively and continuously listen to us as a customer to ensure they deliver innovative solutions and a valuable user experience."
“CyberSecOp is honored to receive our current ranking status and client feedback, and we will continue to prioritize customer satisfaction across the board." Vincent LaRocca, CEO & Co-Founder.
2022 Gartner Peer Insight
Gartner Peer Insights is the firm's platform for rating and reviewing enterprise technology solutions by end-user professionals for end-user professionals. Through user-contributed reviews from people who have actually used the services, the rating system combines expert opinions and peer insights. Peer Insights User Reviews offers a suite of interactive features for technology buyers, including the ability to customize evaluation criteria to create a quadrant view tailored to the user's goals and priorities. The platform employs rigorous methodologies, processes, and quality standards to deliver unbiased research and authentic peer reviews.
What is Gartner’s research?
Gartner research: Trusted insight for executives and their teams
Gartner research, which includes in-depth proprietary studies, peer and industry best practices, trend analysis, and quantitative modeling, enables us to offer innovative approaches that can help you drive stronger, more sustainable business performance.
Gartner research is unique, thanks to:
Independence and objectivity
Our independence as a research firm enables our experts to provide unbiased advice you can trust.
Actionable insights
Gartner’s research is unbiased, containing vital takeaways and recommendations for impactful next steps.
Proprietary methodologies
Our research practices and procedures distill large volumes of data into clear, precise recommendations.
What is Cybersecurity & Security Risk Assessment?
CYBERSECURITY & SECURITY RISK ASSESSMENT
Cybersecurity encompasses the functions, actions, processes, tools, and resources utilized in securing one’s digital presence and cyber network of connected systems, data, and devices. It aims to reduce risk to an organization or entity continuously. It is a complex endeavor where the effort is constant, the dangers are abundant, and visibility is key. Visibility is knowledge, its power, and it can be the difference between staying in business or going out of business. It is the difference between making your customers and clients live better or unintentionally much worse, providing for your employees with a good living or adding to unemployment, and focusing on growing your organization or worrying about how to pay regulatory fines. Yes, visibility is all that and more.
Cybersecurity & Security Risk Assessment Benefits
Now that we’ve established that visibility is essential, let’s look at what it means in the cyber-realm. Visibility is to cyber what doors, windows, locks, roofs, basements, weapons, and fighting or defensive resources are to a zombie attack. Imagine this: you’re in a big house with many rooms, doors, windows, etc., and you are under a zombie attack. You run and close the garage door, lock the front and back doors, shut the windows, and believe you are safe. But you had no idea the roof is only an inch thick and caves in with the slightest weight or some room somewhere in the house had an extra window, and it’s wide open. Think about how all the effort you put into closing all those other doors and windows just went to waste because you missed one and how important it would have been to have known all of that. Game over, right?! That is the power of visibility. Gain knowledge of every weakness and strength and all factors that can potentially become routes to attack or provide defenses.
Cyber Attacks Prevention
In the efforts of ensuring data and systems are protected from cyber-attacks and the plethora of federal, state, and international regulations are met, one of the most powerful tools that provide the needed visibility is a Security Risk Assessment. A Security Risk Assessment conducted by an experienced third party is absolutely key to providing vital visibility into the entire organization’s strengths and weaknesses. But that’s not where a Security Risk Assessment ends. When correctly done, Security Risk Assessments go much further and provide detailed roadmaps to close the identified gaps and maximize the recognized strengths. Security Risk Assessments also hold an organization’s hand and walk them through which gaps pose the most significant risk; and which ones will cost the most or the least. This provides precise risk analysis, ranking all the gaps and risks in detail.
When a third-party Security Risk Assessment is completed and presented, it should provide comprehensive guidance. The guidance offers complete visibility into all you didn’t know, confirmation of what you may have known, and precise advice on achieving a better and more mature security posture inclusive of all the proactive and reactive measures needed.
It's no wonder every Security Framework, international, federal, and state regulation involving IT risk management and cybersecurity emphasizes Security Risk Assessments as a must-have. Don’t be blind to potentially devastating gaps in your organization. Contact us and get your Security Risk Assessment. Cyber-attackers are not waiting, and neither should you.