Cyber Security Readiness & Assessment Service
Every organization faces cybersecurity risks and should take proactive steps to mitigate threats before they become successful attacks. A robust cybersecurity readiness management strategy includes targeted, proactive prevention that can protect a company's reputation, operations, and financial standing. CyberSecOp readiness consulting cybersecurity professionals collaborate with your team to assess specific needs and tailor solutions that improve cyber readiness in the face of mounting cybersecurity risks.
“Measuring ROI in the cybersecurity arena is difficult because the main goal is to avoid a breach”
CyberSecOp Evaluate your cybersecurity readiness on a regular basis
Regular audits and assessments are a tried and true method of assessing cybersecurity readiness. However, these can be costly and time-consuming CyberSecOp team of readiness security experts will work closely with your team to identify and remediate risk on a continuous based.
Analyze your vendors' preparedness for cybersecurity
Third parties are one of the possible cybersecurity readiness weak points in any organization. Risks include complex supply chain attacks on software, like the most recent SolarWinds hack. They can also take place when an attacker moves up the digital supply chain in search of its target by taking advantage of a vendor's lax security measures. Your business may be at risk of a breach if the vendor has access to your data or systems, like a payroll provider.
Cyber Security Readiness & Assessment
Too frequently, organizations concentrate on strengthening security controls rather than preparing for what they will do if an attack starts, which causes expensive delays in discovery and remediation.
Cybersecurity Readiness Holistic Program
Your organization's critical data, as well as the confidentiality, integrity, and availability of that data, can all be ensured with the aid of a security program. Our Cyber Security Operations Consulting Firm, Cybersecurity Program Maturity and Strategy Advisement is committed to assisting companies with a tailored methodology developed over thousands of international engagements to help analyze an organization's current security maturity levels and roadmap in accordance with its particular environment and industry. This thorough methodology includes specific phases to assist organizations as they develop their cybersecurity strategies, such as:
Compliance Security Program
- Virtual CISO (vCISO)
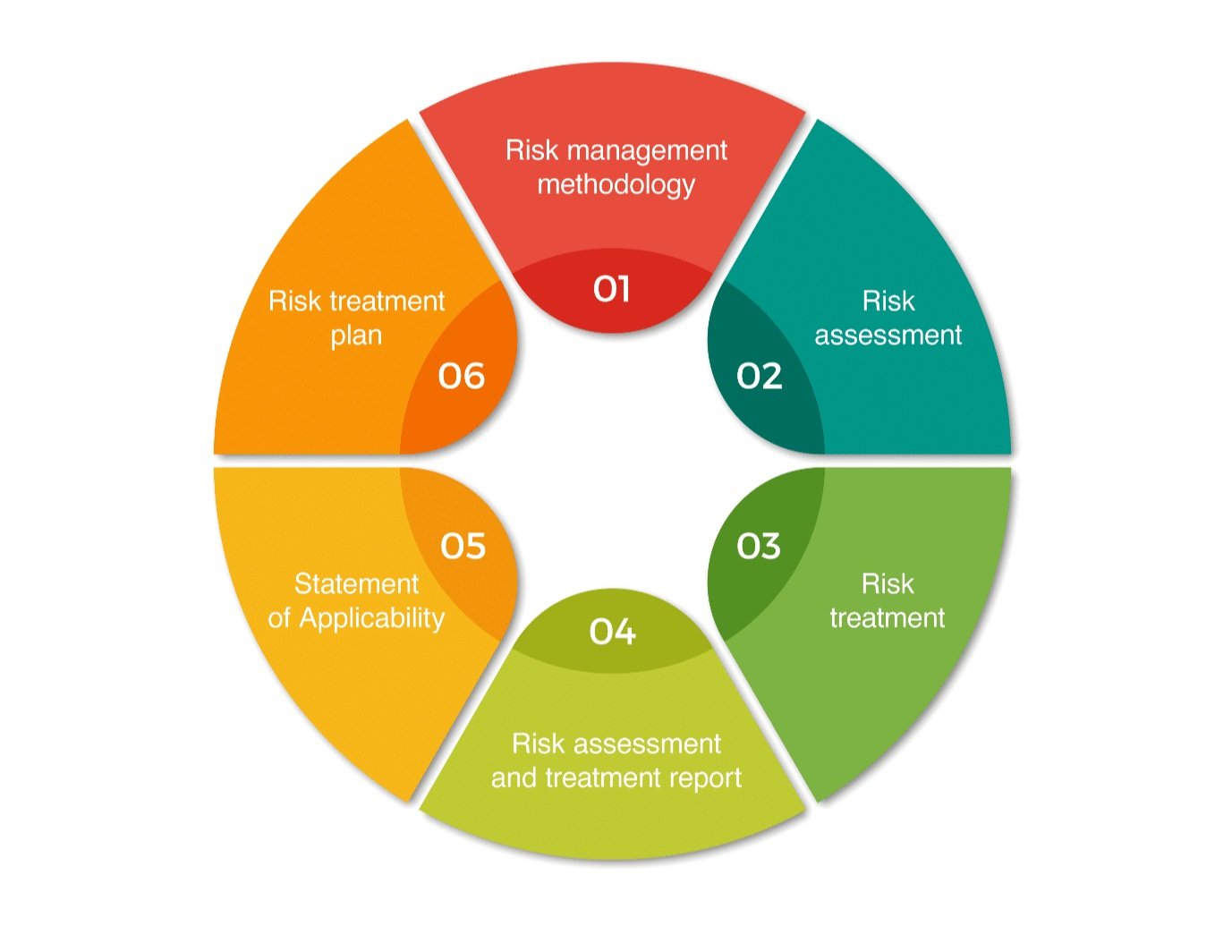
- Risk Assessment and Risk Management
- Program Design & Progam Management
- Develop Policies and Procedures
- Security Strategy and Governance
- Security Incident Response Planning
- Security Architecture Review
- Vendor Risk Management Program
- Vulnerability Management Program
- Dark Web Monitoring
- Security Awareness Training
- C-Level Compliance Reporting
Cyber Security Program
- Virtual CISO (vCISO)
- Security Programs Maturity Assessment
- Managed Vulnerability Service
- Security Policy Review
- Security Incident Response Planning
- Security Architecture Review
- Vendor Risk Management Program
- Vulnerability Management Program
- Phishing and Security Awareness Training
- External Penetration Test
- Threat Advisories
- Executive Briefing
- Red Team Exercise
Why CyberSecOp Cyber Security Program?
Because 85% of cyber attacks involve a human element, countering bad actors falls on each individual in your organization. CyberSecOp offers a variety of security programs, each suited to your company's needs, to assist you in proactively identifying security vulnerabilities and fine-tuning your security approach. To continue growing your software and improving its defenses, we advocate a regular cadence of security assessments and testing.
Cybersecurity Readiness Self Assessment
Cybersecurity continues to be an area of focus for all organizations. Today, businesses of all sizes are under pressure from both hackers and regulators to address the ever-increasing threats from cyber-attacks. Firms like yours experience attacks every day, from a few to a few hundred. When attacks succeed, they often go unnoticed for three to six months. During that time, data may be stolen and penalties incurred.
Take one of our Cybersecurity Readiness Assessment Questionnaires on the left based on your business regulator body; if you just want to see your posture based on your current cyber security standards, please take the Cyber Security Questionnaire below.