Cyber and Information Security Services
Overview: Managed Security - MDR Services - Managed Compliance
CyberSecOp Information Security Service provides security-conscious businesses with products and services that protect them from today's ever-changing security threats. Recognizing the importance of digital identities and system access, CyberSecOp is committed to developing technologies that address the underlying causes of today's security issues. In contrast to security firms that prioritize what they have over what is required, ISS continuously evaluates high-impact solutions through ongoing research and compliance with current regulatory standards. Security starts with your requirements and those of your organization, which are based on objective risk measures and extensive first-hand experience.
Why CyberSecOp Information Security Services
Our Cyber Risk Scoring (CRS) Solution provides consistent, long-term indicators of operational and network security risks based on a diverse set of inputs, global cybersecurity threats, and proprietary analytical methods, assisting organizations and investors in understanding cyber risk behavior and resiliency actions.
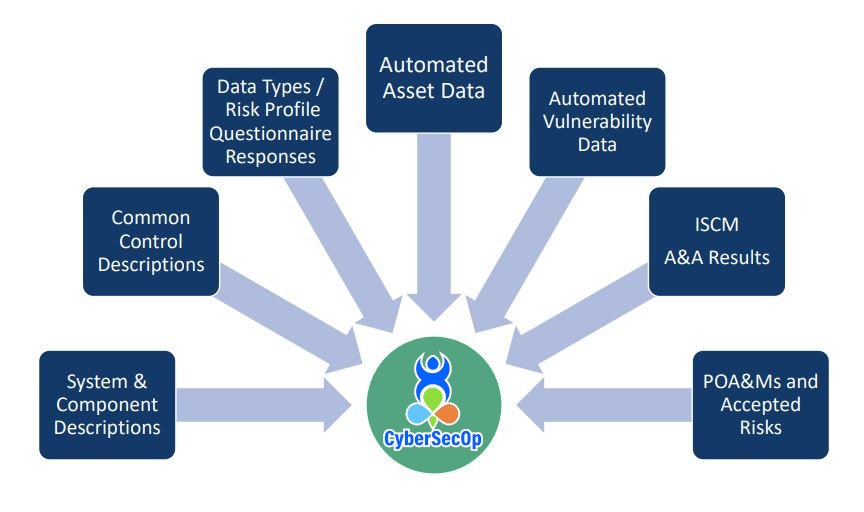
Benefits of Information Security Service
To successfully sustain business investments, quantify cyber risk exposure.
Examine the risks associated with third-party organizations and vendor supply chain dependencies.
Continuously monitor the potential for long-term data breaches across investments and benchmark portfolio performance.
Integrated view of NIST risk posture across the enterprise with quantitative metrics across systems and components
More frequent, meaningful, and actionable risk information to System Owners.
Improved efficiency through automating assessments of specific controls and auto-generation of ATO documentation
A data-driven basis for ongoing authorization decisions
Present the organization’s overall security posture from different perspectives.
Informaiton Security Services by CyberSecOp
CyberSecOp Security offers next-generation cybersecurity services to assist your organization in building cyber resilience from within.
+ Informaiton Security Services
CyberSeccOp provides Information and Informaiton Security Strategy & Design services to give you a better security posture. Our Cybersecurity Services shield your enterprise against threats and strengthen your cyber defenses. You can depend on us to provide comprehensive Information and cyber security services.
+ Informaiton Security Assessment Service
CyberSecOp Informaiton Security Assessments and Auditing services to analyze the maturity of your information security program and identify gaps, weaknesses, and opportunities for improvement. Get our cybersecurity services and identify risks to your business.
+ Vrtual CISO Security Program Service
CyberSecOp Virtual CISO program provides you with wide-ranging expertise for incident response, compliance, and the latest threat intelligence to address information security flaws and execute actionable mitigation strategies. Our cybersecurity services will align with your business strategy.
+ Data Governance Services
CyberSecOp Data Governance Services helps you handle increasingly large volumes of data and the related. Enhancing your Informaiton Security posture and data management.
+ Managed Security Services
Our Managed Security Services, Informaiton Security Services, and Managed Detection and Response (MDR) service provide advanced NexGen managed cyber security services that offer threat intelligence, threat hunting, security monitoring, and cybersecurity incident response services.
+ Third-Party Risk Management Services
Comprehensive Informaiton Security services, including managed security services, Vendor/Third-party cyber security assessment services. We let you know how and what your vendors are doing to secure your data from cyber threats. Do they have a cyber security program?
+ Governance, Risk & Compliance
Aligning your GRC activities to business performance drivers, using frameworks such as NIST, PCI/DSS, ISO, GDPR, NYDFS, and others with our IT security service program.
+ Security Awareness Education
Reveal your organization's employees’ strengths and weaknesses and empower them against cyber-criminals. Our Informaiton Security services ensure your users are ahead of your attackers.
+ Informaiton Security Testing Services
Manage cyber threats proactively with our advanced penetration, and vulnerability testing services.
+ Network Penetration Testing Services – External or Internal
An internal network penetration test is carried out to find out what an attacker could do if they had full access to the network. A test of an internal network's vulnerability can simulate insider threats, such as employees behaving maliciously either intentionally or unintentionally.
+ External Network Penetration Testing**
An external network pen test is intended to evaluate how well perimeter security measures deter and detect attacks as well as find vulnerabilities in internet-facing assets like web, mail, and FTP servers.
+ Wireless Network Penetration Testing Services**
Our wireless assessment methodology, which simulates actual attacks to provide a point-in-time assessment of vulnerabilities and threats to your wireless network infrastructure, is built on the Open Source Security Testing Methodology Manual (OSSTMM) and the Penetration Testing Execution Standard (PTES).
+ Web Application Penetration Testing Services
CyberSecOp leads the industry in web application penetration testing, identifying vulnerabilities in a range of programming languages and environments. From webapps in highly scalable AWS environments to legacy apps in traditional infrastructure, out security experts have helped secure data across the world.
With dozens of zero-day vulnerabilities disclosed and our research circulating on national news outlets, we consistently prove our commitment to top-notch security testing.The architecture, design, and configuration of web applications are evaluated during a web application penetration test, a type of ethical hacking engagement. Cybersecurity risks that could result in unauthorized access and/or data exposure are assessed.
+ Mobile Application Penetration Testing Services
CyberSecOp has experience with multiple security frameworks, and mobile app security standards. Successful mobile app pen testing begins with decades of skills, exemplary customer service, flexible scheduling, and lightning-fast turnaround time. Our team has extensive knowledge of mobile device testing sets us a from other penetration testing services providers.
+ IoT Testing Services
A team of IoT-skilled testers, a strong IoT testing infrastructure (labs, simulators, test racks, etc.), and CyberSecOp's experience in IoT app Testing as a Service (TaaS) support real-time testing of Big Data, Compatibility, IoT Security, Performance, Pilot, Regulatory, Reliability, Upgrade, and smart devices in a dynamic environment.
+ Social Engineering Penetration Testing Services
Penetration testing for social engineering focuses on people, processes, and the vulnerabilities connected to them. The goal of a social engineering attack typically entails persuading individuals to reveal sensitive information or engage in beneficial behavior for the attacker, preferably without their knowledge. Information security programs frequently need to perform regular penetration tests to simulate the threat of social engineering attacks. Benefits of social engineering tests include:
Identify vulnerabilities relating to attacks that leverage people and process. Understand the likely impact of an attacker that uses social engineering. Gain insight into what people and process defenses are currently working well. Get assurance that includes consideration of real-world threats such as phishing
+ Red Team Attack Simulation Services
CyberSecOp Red Team Advanced Penetration Testing starts with a clear understanding of your vulnerabilities and risk; penetration testing plays an essential role. We have performed over 100 red team exercises on both corporate office and industrial plant locations, and we have the resources, methodology, and experience to perform these tests in a safe manner that does not impose any operational risk to our clients
With our red team, we will perform Application Penetration Testing, Network Penetration Testing, Vulnerability Testing, Phishing Testing, and Social Engineering to find the weak spots in your critical assets/employees and recommend corrective action before attackers exploit them, sabotage your business or steal your confidential data.
What exactly is the distinction between cybersecurity and information security?
The terms information security and cybersecurity are frequently used interchangeably. InfoSec is an important component of cybersecurity, but it only refers to data security processes. Cybersecurity is a broader term that encompasses InfoSec.
What is an information security management system (ISMS)?
An ISMS is a set of guidelines and processes to assist organizations in a data breach. Businesses that have a formal set of guidelines can reduce risk and ensure work continuity in the event of a staff change. ISO 27001 is a well-known company's ISMS specification.
CyberSecOp cyber security services reduce risk through Advisory services and security product expertise. We are a trusted advisor for all your cyber security needs. Let our specialists in cybersecurity services help you create and implement a comprehensive information security solution to prevent cyber attacks.
Cybersecurity as a Service (CSaaS)
Proactive Cybersecurity as a Service (CSaaS) to mitigate cyber risks, every business needs a depth defense, including IT security solutions and cybersecurity experts who can deploy and monitor them.
Transform your cybersecurity, strengthen it and become proactive, effective, and resilient. Cybersecurity is a core business requirement, providing a secure foundation to transform your enterprise and support your business. Ready to see how CyberSecOp Cyber Security Services can help?