CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Holistic Ransomware Security Approach
Do you have a holistic approach for security against ransomware? To prevent events from escalating, consider immediate containment and expert remediation assistance. Ransomware attacks are rampant, and include hackers locking up computer systems and demanding a payment to unlock them. Ransomware has had devastating effects on our infrastructure and economy, impeded emergency responders, stalled tax payments and forced government offices back to pen-and-paper operations for weeks on end.
80% of those who paid their ransom were attacked again, and not even security firms are immune to these attacks.
What is Ransomware?
Ransomware is a form of malicious software (malware) that is designed to encrypt files on a device, making the files and the systems that rely on them unusable. Malicious actors then demand a ransom payment, usually in the form of cryptocurrency, in exchange for decryption. These malicious actors may also make extortion demands, by threating to release stolen data if a ransom is not paid, or may come back after the fact and demand an additional payment in order to prevent the release of stolen data.
Recent Breach of a Top Security Firm
Accenture, one of the largest security firms around, confirmed in August 2021 that it was hit by a ransomware attack, with a hacker group using the LockBit ransomware reportedly threatening to release the company’s data and sell insider information.
Previously, the cybersecurity firm FireEye had been the first call for help at government agencies and international companies who had been hacked by sophisticated attackers. Yet on Dec 8, 2020, FireEye announced it had been breached, and not just data but also some of its most valuable tools had been stolen.
Ransomware Impact
The impact of a successful ransomware deployment includes both technical and non-technical challenges, and can be crippling to business operations. Modern-day attackers have developed advanced techniques that now require a holistic security risk mitigation strategy, inclusive from the board to technical practitioners.
The impact of ransomware can include:
· Temporary, and possibly permanent, loss of your company's data
· A complete shutdown of your company's operations
· Financial loss as a result of revenue-generating operations being shut down
· Financial loss associated with the cost of remediation efforts
· Permanent damage to your company's reputation
How Can CyberSecOp Help Your Organization?
Holistic Security Risk Mitigation Strategy
A holistic approach to cybersecurity can address the following components and their implications for governance, organizational structures, and processes. Our holistic security program includes a risk management program, which provides an accurate overview of the risk landscape and governing principles that ensure accurate risk reporting. We address:
Assets: Clearly defining critical assets
Controls: Differentiated controls to balance security with agility
Processes: State-of-the-art and fully tested procedures for optimal security and remediation
Organization: Bringing the right skills, most efficient decision making, and effective enterprise-wide cooperation into your organization
Governance: Investments in operational resilience, prioritized based on deep transparency into cyber risks including third parties and vendors, covering of the whole value chain
Patches: Keeping your network up to date with the latest software patches
Software Mitigations: Using robust antivirus and firewall protections in your network
Backups: Backing up data securely and separately from your network, and routinely testing restoring from backups
Incident Response Services
Scoping and Investigation
The CyberSecOp Incident Response (IR) Team conducts forensic analysis to identify root causes and ensure rapid containment of ongoing attacks. This swiftness to action helps prevent escalation.
Services and Expert Guidance
CyberSecOp IR Team remediates issues throughout the network and implements updates to configurations, architecture, and tooling.
Advanced Threat Analysis
The CyberSecOp Team conducts in-depth investigations including root cause analysis, malware reverse engineering and comprehensive incident reporting.
How Does Ransomware Infect my Network?
Ransomware, like other forms of malware, seeks to take advantage of poor security practices employed by employees and system administrators. According to the Internet Crime Complaint Center (IC3) the most common methods of infection are:
Email Phishing: This social engineering attack vector occurs when a cyber-criminal sends an email which appears to be legitimate, but in fact contains a link to a malicious website or document with a malicious script, which then infects the recipient’s computer and associated network.
Remote Desktop Protocol (RDP) Vulnerabilities: RDP is a type of software that allows individuals to control the resources of another computer over the internet. RDP is commonly used by employees working remotely and by system administrators to manage computers from a distance.
Software Vulnerabilities: These vulnerabilities are flaws in the code of a piece of software (like Microsoft Word) that can be exploited by threat actors to gain control of a system to deploy malware. A common example would be “macros” that get installed within Microsoft Word or Microsoft Excel that lead to infection.
Best Practices and remedial measures
Users and administrators are advised to take the following preventive measures to protect their computer networks from ransomware infection/ attacks:
Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
Check regularly for the integrity of the information stored in the databases.
Regularly check the contents of backup files of databases for any unauthorized encrypted contents of data records or external elements, (backdoors /malicious scripts.)
Ensure integrity of the codes /scripts being used in database, authentication and sensitive systems
Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
Keep the operating system third party applications (MS office, browsers, browser Plugins) up-to-date with the latest patches.
Application white listing/Strict implementation of Software Restriction Policies (SRP)to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
Maintain updated Antivirus software on all systems
Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser
Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
Disable remote Desktop Connections, employ least-privileged accounts. Limit users who can log in using Remote Desktop, set an account lockout policy. Ensure proper RDP logging and configuration.
Restrict access using firewalls and allow only to selected remote endpoints, VPN may also be used with dedicated pool for RDP access
Use strong authentication protocol, such as Network Level Authentication (NLA) in Windows.
Additional Security measures that may be considered are
Use RDP Gateways for better management
Change the listening port for Remote Desktop
Tunnel Remote Desktop connections through IPSec or SSH
Two-factor authentication may also be considered for highly critical systems
If not required consider disabling, PowerShell / windows script hosting.
Restrict users' abilities (permissions) to install and run unwanted software applications.
Enable personal firewalls on workstations.
Implement strict External Device (USB drive) usage policy.
Employ data-at-rest and data-in-transit encryption.
Consider installing Enhanced Mitigation Experience Toolkit, or similar host-level anti-exploitation tools.
Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
Carry out vulnerability Assessment and Penetration Testing (VAPT) and information security audit of critical networks/systems, especially database servers from CERT-IN empaneled auditors. Repeat audits at regular intervals.
Individuals or organizations are not encouraged to pay the ransom, as this does not guarantee files will be released. Report such instances of fraud to CERT-In and Law Enforcement agencies
Our IT & cybersecurity consulting service protects you from cyber criminals in myriad ways. From implementing a cybersecurity program, which include a written information security program and cybersecurity assessment, to purchasing our best-in-class cybersecurity consulting and IT security solutions, engaging with CyberSecOp will lead you in the right direction towards an enhanced security stance. CyberSecOp is an ISO 27001 Certification Organization - join thousands of businesses by putting your security in our hands.
Facilitation of Ransomware Payment Sanction Risk
US Treasury Department Issues Ransomware Advisory
The ransomware advisories provides guidances and tools to recognize, resist, and report attacks.
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) is issuing this advisory to highlight the sanctions risks associated with ransomware payments related tomalicious cyber-enabled activities. Demand for ransomware payments has increased during the COVID-19 pandemic as cyber actors target online systems that U.S. persons rely on to continue conducting business. Companies that facilitate ransomware payments to cyber actors on behalf of victims, including financial institutions, cyber insurance firms, and companies involved in digital forensics and incident response, not only encourage future ransomware payment demands but also may risk violating OFAC regulations. This advisory describes these sanctions risks and provides information for contacting relevant U.S. government agencies, including OFAC, if there is a reason to believe the cyber actor demanding ransomware payment may be sanctioned or otherwise have a sanctions nexus.
Facilitating ransomware is harmful long term
Not only do ransomware payments fuel future attacks, OFAC explained it also threatens US national security interests given their profit and later ability to advance their cause. Paying ransom to a sanctioned entity or jurisdiction could fund activities in conflict with national interests.
What is Ransomware? Ransomware is a form of malicious software (“malware”) designed to block access to a computer system or data, often by encrypting data or programs on information technology systems to extort ransom payments from victims in exchange for decrypting the information and restoring victims’ access to their systems or data. In some cases, in addition to the attack, cyber actors threaten to publicly disclose victims’ sensitive files. The cyber actors then demand a ransomware payment, usually through digital currency, in exchange for a key to decrypt the files and restore victims’ access to systems or data.
Ransomware Payments with a Sanctions Nexus Threaten U.S. National Security Interests
Facilitating a ransomware payment that is demanded as a result of malicious cyber activities may enable criminals and adversaries with a sanctions nexus to profit and advance their illicit aims. For example, ransomware payments made to sanctioned persons or to comprehensively sanctioned jurisdictions could be used to fund activities adverse to the national security and foreign policy objectives of the United States. Ransomware payments may also embolden cyber actors to engage in future attacks. In addition, paying a ransom to cyber actors does not guarantee that the victim will regain access to its stolen data.
Facilitating Ransomware Payments on Behalf of a Victim May Violate OFAC Regulations
Under the authority of the International Emergency Economic Powers Act (IEEPA) or the Trading with the Enemy Act (TWEA),9 U.S. persons are generally prohibited from engaging in transactions, directly or indirectly, with individuals or entities (“persons”) on OFAC’s Specially Designated Nationals and Blocked Persons List (SDN List), other blocked persons, and those covered by comprehensive country or region embargoes (e.g., Cuba, the Crimea region of Ukraine, Iran, North Korea, and Syria). Additionally, any transaction that causes a violation under IEEPA, including transactions by a non-U.S. person which causes a U.S. person to violate any IEEPA-based sanctions, is also prohibited. U.S. persons, wherever located, are also generally prohibited from facilitating actions of non-U.S. persons, which could not be directly performed by U.S. persons due to U.S. sanctions regulations. OFAC may impose civil penalties for sanctions violations based on strict liability, meaning that a person subject to U.S. jurisdiction may be held civilly liable even if it did not know or have reason to know it was engaging in a transaction with a person that is prohibited under sanctions laws and regulations administered by OFAC.
Victims of Ransomware Attacks Should Contact Relevant Government Agencies OFAC encourages victims and those involved with addressing ransomware attacks to contact OFAC immediately if they believe a request for a ransomware payment may involve a sanctions nexus. Victims should also contact the U.S. Department of the Treasury’s Office of Cybersecurity and Critical Infrastructure Protection if an attack involves a U.S. financial institution or may cause significant disruption to a firm’s ability to perform critical financial services.
U.S. Department of the Treasury’s Office of Foreign Assets Control
- Sanctions Compliance and Evaluation Division: ofac_feedback@treasury.gov;
- (202) 622-2490 / (800) 540-6322
- Licensing Division: https://licensing.ofac.treas.gov/; (202) 622-2480
U.S. Department of the Treasury’s Office of Cybersecurity and Critical Infrastructure
- Protection (OCCIP)
- OCCIP-Coord@treasury.gov; (202) 622-3000
- Financial Crimes Enforcement Network (FinCEN)FinCEN Regulatory Support Section: frc@fincen.gov 12 See FinCEN Guidance, FIN-2020-A00X, “Advisory on Ransomware and the Use of the Financial System to Facilitate Ransom Payments,” October 1, 2020, for applicable anti-money laundering obligations related to financial institutions in the ransomware context.
Contact Information for Other Relevant U.S. Government Agencies:
Federal Bureau of Investigation Cyber Task Force
U.S. Secret Service Cyber Fraud Task Force
Cybersecurity and Infrastructure Security Agency
Homeland Security Investigations Field Office
Cybersecurity Risks in a Pandemic: What you need to know
The COVID-19 pandemic has alerted many organizations to gaps in their information security infrastructure heretofore unrealized. Most of these deficiencies have been revealed as a direct outcome of the shift from a workforce-in-place physical environment centered around a fixed and determinable worksite location to a distributed, unstructured environment where most employees and individuals are working remotely.
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations.
The lack of a centralized workspace raises a multiplicity of information security concerns, including but not limited to the following:
1. Does the company have an established Work-From-Home (WFH) information security policy, and if not, how is remote worker security managed?
2. Are employees adequately trained to work remotely, and do they have the appropriate tools at their disposal to ensure the preservation of the security environment?
3. How does the organization manage mobile device and laptop security, including encryption?
4. Control and testing of the commercial VPN?
5. Does the organization maintain a comprehensive data loss protection policy?
6. How, if at all does the organization address data loss protection?
7. Does the organization have a breach response plan for mobile and remote WFH employees?
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations. Our skilled team of information security professionals can provide a comprehensive assessment of your information security framework and suggest remediation and complementary additions to your existing framework, as the case may be.
There are several things to consider if and when the time comes for firms to return to the office. CyberSecOp recommends:
Third-Party network risk assessment
Operational Responses to Security Incidents
Work from Home Security
Virtual Meeting Applications
Updates and Patches
A full virus scan on workstations returning to the office
Full Windows/Mac updates
Review Wi-Fi connections on returning devices: Some people may come back and still connect to Optimum Wi-Fi (This can be very risky)
Delete any accounts not for company use
Provisioning devices employees may have bought in haste (Hardening AV adding to the domain)
Mobile device management strategy for new mobiles, or devices that employees are using more
Pandemic Policy, Cybersecurity Policy Wireless policy
It is important for organizations to foresee possible consequences transitioning from working remotely to returning to the office. CyberSecOp can help facilitate this transition.
AUTHOR: Michael Young
Ransomware Revenue 2019 - Demand Cost Increases
Ransomware is a type of malware that stops users from accessing their data until a ransomware payment is arranged. The money is usually paid in cryptocurrencies to avoid any kind of detection. Ransomware criminals trick you into clicking on infected links. They usually do this by copying the general look of an email to mask their nefarious intentions. Organizations interviewed by CyberSecOp say they experience data loss and major downtime as the result of a ransomware attack. Both of these outcomes are extremely costly for a business, especially larger ones with hundreds of employees. Significant downtime can result in millions of dollars of lost revenue and decreased consumer trust.
Cybercriminals Career Path is Ransomware
If you were considering becoming a cybercriminal or were perhaps a traditional villain looking to upgrade your skills for the 21st century, I’m sure your business model of choice would be running a ransomware operation. You would, thanks to the simplicity of platforms like Ransomware as a Service and the willingness of victims to pay ransomware fees.
The reason why Ransomware most common attack vector
The main reason for the runaway success of ransomware as a malware attack vector is its effectiveness and ability to generate money for cybercriminals. Anonymous payment services like Bitcoin make ransomware payment simple for victims and risk-free for the ransomware owners. Companies are even starting to keep a Bitcoin ransom ready if they are affected and cannot recover from the attack.
Ransomware big newsmakers
The biggest news-maker for 2019 is the Baltimore City government. The city’s computer system was hit with a ransomware infection in May 2019 that kept the city’s government crippled for over a month. Estimates put the cost to recover at over 18 million dollars, although the cybercriminal behind the ransomware only demanded $76,000 worth of Bitcoin. The attack reportedly impacted vaccine production, ATMs, airports, and hospitals. Just about a year earlier, the Atlanta city government spent over $17 million to recover from a ransomware attack that demanded $52,000 in Bitcoin.
The big tech giants are getting hit by ransomware too
Popular software as a service (SaaS) applications are being targeted by ransomware too. A study involving several multiple service providers found that Dropbox, Office 365, G Suite, Azure, and Amazon Web Services have experienced ransomware attacks in some form.
Ransomware Demand cost increases
At the same time, the average ransomware demands have increased rapidly to $36,000 in the second quarter of 2019. But this number understates the risk as perpetrators have adopted a more sophisticated pricing model which charges larger organizations much higher ransoms to unlock their data. Rivera Beach, FL, for example, had to pay $600,000 to unlock the city records encrypted by a ransomware gang while Korean hosting company Nayana paid $1m to unlock 3,400 hosted websites. Refusing to pay can cost even more as Norwegian aluminum maker Norsk Hydro learned when they spent $58m in the first half of 2019 to remediate the ransomware attack they experienced in March. The company’s Q1 profit also fell 82% due to production downtime caused by the attack. The implications for security professionals of these trends are clear. The time has come to move from a strictly defensive posture vis-à-vis ransomware to a more offensive strategy focused on finding and fixing vulnerabilities that can be exploited by ransomware.
98% of ransomware profits went through the cryptocurrency trading platform BTC
Ransomware Attack: Threats, and Countermeasures
When you combine cryptography with malware, you get a very dangerous mix of problems. This is a type of computer virus that goes by another name, “ransomware”. This type of virus is part of a field of study called “cryptovirology”. Through the use of techniques called phishing, a threat actor sends the ransomware file to an unknowing victim. If the file is opened it will execute the virus payload, which is malicious code. The ransomware runs the code that encrypts user data on the infected computer or host. The data are user files like documents, spreadsheets, photos, multimedia files and even confidential records. The ransomware targets your personal computer files and applies an encryption algorithm like RSA which makes the file inaccessible. The only way to access them is if the user pays a ransom to the threat actor by following instructions which appear encoded into the encrypted files. Thus it is called ransomware, because a form of payment is demanded in order to fix the problem.
Once they have all publicly available email addresses, the fun starts. The more of your email addresses that are floating out there, the bigger your attack footprint is, and the higher the risk is. It’s often a surprise how many addresses are actually out there. Now they can send all employees an email supposedly coming from Accounting, Human Resources, the CEO or perhaps the mail room, and social engineer your users to click on a link. almost 90 percent of attack are done via the internet, based on the new software model, and yes the bad guys are also moving to the cloud. Software is shifting away from locally-installed apps to Software as a Service web applications that run in the cloud. Criminals are cashing in on this trend, which has led to the creation of Ransomware as a Service (RaaS), a growing threat to business.
RaaS refers to various online malware exploits that bad actors can use to attack the IT assets of businesses and individuals. These attack programs are created by criminal entrepreneurs who sell their services to other criminals. The people who buy these programs then extort or blackmail their victims by holding computer systems to ransom.
How does Ransomware spread?
Ransomware is typically spread through phishing emails that contain malicious attachments. These emails appear to come from a legitimate source and give a compelling reason that the document is important. Malicious attachments are often PDF, ZIP, DOC, XLS, PPT files that appear as invoices, legitimate business documents, or other work-related files. In some cases, Ransonware may end up on your computer by visiting infected web sites. To avoid malicious drive-by downloads, ensure that antivirus and all installed software is up-to-date.
How to Mitigate the Risk of Ransomware Infections
These recommendations are not comprehensive but provide general best practices.
Securing Networks and Systems
Have an incident response plan that includes what to do during a ransomware event.
Backups are critical. Use a backup system that allows multiple iterations of the backups to be saved, in case a copy of the backups includes encrypted or infected files. Routinely test backups for data integrity and to ensure it is operational.
Use antivirus and anti-spam solutions. Enable regular system and network scans with antivirus programs enabled to automatically update signatures. Implement an anti-spam solution to stop phishing emails from reaching the network. Consider adding a warning banner to all emails from external sources that reminds users of the dangers of clicking on links and opening attachments.
Disable macros scripts. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full office suite applications.
Keep all systems patched, including all hardware, including mobile devices, operating systems, software, and applications, including cloud locations and content management systems (CMS), patched and up-to-date. Use a centralized patch management system if possible. Implement application white-listing and software restriction policies (SRP) to prevent the execution of programs in common ransomware locations, such as temporary folders.
Restrict Internet access. Use a proxy server for Internet access and consider ad-blocking software. Restrict access to common ransomware entry points, such as personal email accounts and social networking websites.
Apply the principles of least privilege and network segmentation. Categorize and separate data based on organizational value and where possible, implement virtual environments and the physical and logical separation of networks and data. Apply the principle of least privilege.
Vet and monitor third parties that have remote access to the organization’s network and/or your connections to third parties, to ensure they are diligent with cybersecurity best practices.
Participate in cybersecurity information sharing programs and organizations, such as MS-ISAC and InfraGard.
Securing the End User
Provide social engineering and phishing training to employees. Urge them not to open suspicious emails, not to click on links or open attachments contained in such emails, and to be cautious before visiting unknown websites.
Remind users to close their browser when not in use.
Have a reporting plan that ensures staff knows where and how to report suspicious activity.
Responding to a Compromise/Attack
Immediately disconnect the infected system from the network to prevent infection propagation.
Call CyberSecOp.com Ransomware Response Team: They provide remediation and bitcoin payment services.
Determine the affected data as some sensitive data, such as electronic protected health information (ePHI) may require additional reporting and/or mitigation measures.
Determine if a decryptor is available. Online resources such as No More Ransom! can help.
Restore files from regularly maintained backups.
Report the infection. It is highly recommended that SLTT government agencies report ransomware incidents to MS-ISAC. Other sectors and home users may report to infections to local Federal Bureau of Investigation (FBI) field offices or to the Internet Crime Complaint Center (IC3).
Ransomware Checker & Removal Tools
Are Users Your Weakest Link - To Your Cybersecurity Posture
Humans remain the weak link in corporate data protection
Humans remain the weak link in corporate data protection, but you might be surprised that it isn't only rank-and-file employees duped by phishing scams who pose risks. Some companies are lulled into a false sense of cybersecurity by vendors. You read that right, Some enterprises believe the shiny new technologies they've acquired will protect them from anything.
As we continue to build defense in depth and deploy security appliances utilizing AI and other emerging technologies, attackers will continue to pivot to the perennial weak spot: the users. Recently I hosted the Social Engineering Capture The Flag competition at Hackfest in Quebec, and similar to last year, the results were sobering. Every single targeted company had employees that gave detailed information over the phone on their OS and service pack level, and 88 percent gave detailed information on the browser they were using. Three quarters went to a URL that they were given over the phone. The information that the companies bled was disheartening but not shocking. Until we train employees to trust their instincts and tell them it's okay to say no to a customer, things won't change. In the current environment where companies ask their customers to leave a positive review online, employees increasingly feel less empowered to terminate a call they feel is suspicious. Your friendly neighborhood hacker is happy to exploit this weakness.
Billions being send on security tools
The threat of cyber crime has created a significant increase in interest on the topic of cyber security, with organizations spending billions of dollars to protect themselves against a fast evolving array of current and potential future threats. Many spend heavily on monitoring, surveillance and software; however, they often neglect the risk exposure created by their own people – and, in this digital age, by their customers.
Businesses are losing the fight, pay ransom, or lose their lively hood
Businesses are forced to make exceedingly difficult decisions. On one hand, it feels wrong to negotiate with the cybercriminals and give them what they want. On the other hand, the looming financial hit and business interruption is typically far more detrimental than the payoff amount. If business owners don’t engage with the ransomers, they face the prospect that they, and their employees, may lose their livelihood. I see ransomware as a continuing cyber threat in 2019 and beyond. It’s up to business owners to implement the best security practices and ensure that their employees are properly trained to identify and avoid potential threats.
MSSP Cybersecurity & Managed Detection and Response
MSSP Cybersecurity & Managed Detection and Response
Managed detection and response enables a proactive approach to security with its ability to detect and fully analyze threats and promptly respond to incidents. CyberSecOp Threat intelligence is one of the key aspects our security consultants used to help organizations make decisions on how to combat threats. Through managed detection and response, organizations can take advantage of the threat intelligence capabilities of security experts.
How Managed Detection and Response Provides Effective Threat Intelligence
Capture full visibility across your entire IT environment
Detect the most advanced threats (known and unknown) designed to bypass your traditional perimeter security controls, even when no malware is used
Expose threat actors currently hiding in your environment
Gain 24x7 monitoring by an advanced team of security experts that are specially trained to analyze advanced threats, determine the severity of any incidents and provide actionable guidance to remediate
Quickly elevate the alerts that matter most so you can focus limited resources where it matters most
Managed Detection and Response Service
Managed Detection and Response (MDR) is an all-encompassing cybersecurity service used to detect and respond to cyber-attacks. Using the best of signature, behavioral and anomaly detection capabilities, along with forensic investigation tools and threat intelligence, human analysts hunt, investigate and respond to known and unknown cyber threats in real time 24x7x365. Get Managed Detection and Response Services for your business www.cybersecop.com.
Ransomware Cyberattack - 92% of MSSPs Expect Ongoing Attacks
Ransomware is the leading cyberattack experienced by small and medium-sized businesses (SMBs), according to a survey of more than 2,400 managed service providers (MSSPs) conducted by data protection company Datto.
Datto’s State of the Channel Ransomware Report provides unique visibility into the ransomware epidemic from the perspective of the IT Channel and the SMB clients who are dealing with these infections on a daily basis. The report provides a wealth of detail on ransomware, including year-over-year trends, frequency, targets, impact, and recommendations for ensuring recovery and continuity in the face of the growing threat.
Key findings from Datto’s “State of the Channel Ransomware Report” included:
79 percent of MSSPs reported ransomware attacks against customers.
85 percent indicated that victims had antivirus software installed, 65 percent reported victims had email/spam filters installed and 29 percent reported victims used pop-up blockers.
89 percent are “highly concerned” about ransomware attacks.
92 percent predict the number of ransomware attacks will continue at current, or worse, rates.
MSPs ranked phishing emails as the top ransomware delivery method, followed by malicious websites, web ads and clickbait.
The average requested ransom for SMBs is roughly $4,300, while the average cost of downtime related to such an attack is approximately $46,800.
The number of MSPs reporting OS/iOS attacks increased by nearly 500 percent year over year in the first six months of 2018.
No single solution is guaranteed to prevent such attacks, Datto indicated. Conversely, SMBs require a multilayered approach to identify and stop ransomware attacks before they cause brand reputation damage, revenue loss and other problems.
How Can SMBs Address Ransomware Attacks?
CyberSecop offered the following recommendations to help SMBs safeguard their data and assets against such attacks:
Leverage business continuity and disaster recovery (BCDR) technology. BCDR technology won’t stop ransomware attacks; instead, it helps an SMB determine how to limit downtime and maintain operations despite a ransomware attack.
Provide cybersecurity training. By offering regular and mandatory cybersecurity training, an SMB can ensure all of its employees can identify and avoid potential phishing scams that otherwise lead to such an attack.
Employ a dedicated cybersecurity professional. It may be difficult for an SMB to hire a full-time cybersecurity professional. Fortunately, working with an MSSP allows an SMB to receive cybersecurity monitoring and other security services.
Ransomware Business Impacts, Ransomware Business Cost
Projecting the overall cost of a ransomware attack can be tricky for security executives considering the many factors that can come into play when responding to and recovering from one. Information from numerous previous incidents show the costs go well beyond any demanded ransom amount and the costs associated with cleaning infected systems.
Ransomware is defined as a form of malicious software that is designed to restrict users from accessing their computers or files stored on computers till they pay a ransom to cybercriminals. Ransomware typically operates via the crypto virology mechanism, using symmetric as well as asymmetric encryption to prevent users from performing managed file transfer or accessing particular files or directories. Cybercriminals use ransomware to lock files from being used assuming that those files have extremely crucial information stored in them and the users are compelled to pay the ransom in order to regain access.
Ransomware History
It’s been said that Ransomware was introduced as an AIDS Trojan in 1989 when Harvard-educated biologist Joseph L. Popp sent 20,000 compromised diskettes named “AIDS Information – Introductory Diskettes” to attendees of the internal AIDS conference organized by the World Health Organization. The Trojan worked by encrypting the file names on the customers’ computer and hiding directories. The victims were asked to pay $189 to PC Cyborg Corp. at a mailbox in Panama.
From 2006 and on, cybercriminals have become more active and started using asymmetric RSA encryption. They launched the Archiveus Trojan that encrypted the files of the My Documents directory. Victims were promised access to the 30-digit password only if they decided to purchase from an online pharmacy.
After 2012, ransomware started spreading worldwide, infecting systems and transforming into more sophisticated forms to promote easier attack delivery as the years rolled by. In Q3, about 60,000 new ransomware was discovered, which doubled to over 200,000 in Q3 of 2012.
The first version of CryptoLocker appeared in September 2013 and the first copycat software called Locker was introduced in December of that year.
Ransomware has been creatively defined by the U.S. Department of Justice as a new model of cybercrime with a potential to cause impacts on a global scale. Stats indicate that the use of ransomware is on a steady rise and according to Veeam, businesses had to pay $11.7 on average in 2017 due to ransomware attacks. Alarmingly, the annual ransomware-induced costs, including the ransom and the damages caused by ransomware attacks, are most likely to shoot beyond $11.5 billion by 2019.
Ransomware Business Impacts Can Be Worrisome
Ransomware can cause tremendous impacts that can disrupt business operations and lead to data loss. The impacts of ransomware attacks include:
Loss or destruction of crucial information
Business downtime
Productivity loss
Business disruption in the post-attack period
Damage of hostage systems, data, and files
Loss of reputation of the victimized company
You will be surprised to know that apart from the ransom, the cost of downtime due to restricted system access can bring major consequences. As a matter of fact, losses due to downtime may cost tens of thousands of dollars daily.
As ransomware continues to become more and more widespread, companies will need to revise their annual cybersecurity goals and focus on the appropriate implementation of ransomware resilience and recovery plans and commit adequate funds for cybersecurity resources in their IT budgets.
Consider the following examples. The Erie County Medical Center (ECMC) in Buffalo, NY, last July estimated it spent $10 million responding to an attack involving a $30,000 ransom demand. About half the amount went toward IT services, software, and other recovery-related costs. The other half stemmed from staff overtime, costs related to lost revenues, and other indirect costs. ECMC officials estimated the medical center would need to spend hundreds of thousands of dollars more on upgrading technology and employee awareness training.
Public records show that the City of Atlanta spent almost $5 million just in procuring emergency IT services following a March 2018 ransomware attack that crippled essential city services for days. The costs included those associated with third-party incident response services, crisis communication, augmenting support staff and subject matter expert consulting services.
In Colorado, Gov. John Hickenlooper had to set aside $2 million from the state disaster emergency fund after ransomware infected some 2,000 Windows systems at CDOT, the state department of transportation, this February. In less than eight weeks, CDOT officials spent more than half that amount just returning systems to normal from the attack.
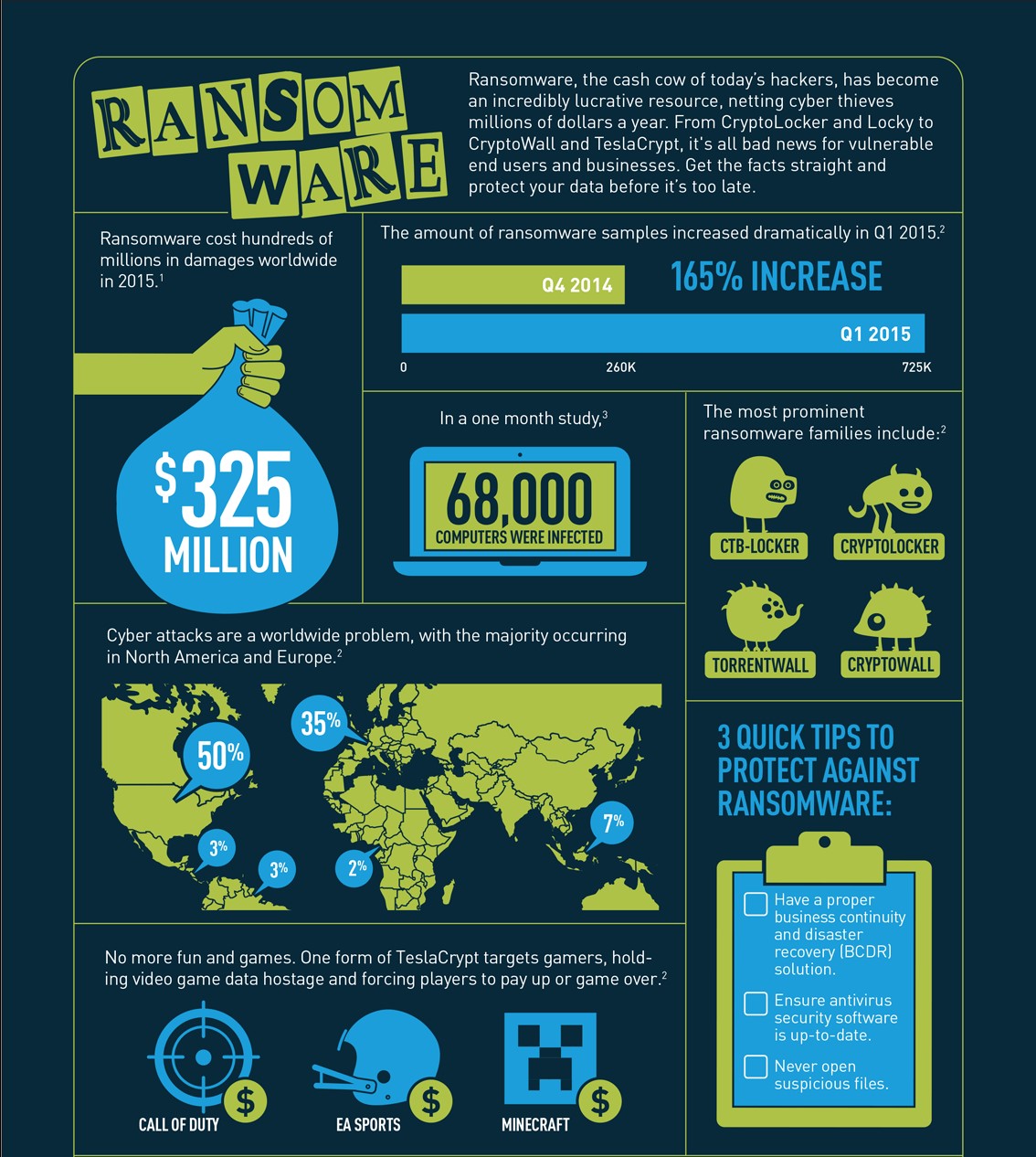
Not surprisingly, industry estimates relating to ransomware damages have soared recently. Cybersecurity Ventures, which pegged ransomware costs at $325 million in 2015, last year estimated damages at $5 billion in 2017 and predicted it would exceed $11.5 billion in 2019.
For security executives trying to prepare a total ransomware cost estimate, the key is not to get fixated on the ransom amount itself. Even if you end up paying it to recover your data—something that most security analysts advocate against—the actual costs of the attack in most cases will end up being greater.
FBI: Protecting Your Networks from Ransomware
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
What is Ransomware”
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment. Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails. For additional information on Avoiding Social Engineering and Phishing Attacks.
Ransomware Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Ransomware Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. USG does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
How Law Enforcement Can Help
Any entity infected with ransomware should contact law enforcement immediately. Law enforcement may be able to use legal authorities and tools that are unavailable to most organizations. Law enforcement can enlist the assistance of international law enforcement partners to locate the stolen or encrypted data or identify the perpetrator. These tools and relationships can greatly increase the odds of successfully apprehending the criminal, thereby preventing future losses.
Federal law enforcement places a priority on conducting cyber investigations in a manner that causes minor disruption to a victim entity’s normal operations and seeks to work cooperatively and discreetly with that entity. Federal law enforcement uses investigative measures that avoid unnecessary downtime or displacement of a company’s employees. Federal law enforcement closely coordinates its activities with the affected organization to avoid unwarranted disclosure of information.
As an affected entity recovers from a cybersecurity incident, the entity should initiate measures to prevent similar incidents. Law enforcement agencies and the Department of Homeland Security’s National Cybersecurity and Communications Integration Center can assist organizations in implementing countermeasures and provide information and best practices for avoiding similar incidents in the future. Additionally, the affected organization should conduct a post-incident review of their response to the incident and assess the strengths and weaknesses of its incident response plan.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor ” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising .
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
HOW DOES RANSOMWARE WORK?
HOW DOES RANSOMWARE WORK?
Ransomware infections occur when a user opens a malicious email attachment, clicks on a malicious link, or visits a website infected with malicious code, known as a drive-by download.
Once a system is infected, the ransomware contacts a command and control (C2) server to generate an encryption key and begins encrypting files on the victim’s machine.
The ransomware runs quietly in the background performing in-depth searches of all disk folders, including removable drives and network shares, and encrypts as many files as it can.
Ransomware may also delete Shadow Volume Copies, destroy restore points, and overwrite free disk space to prevent victims from recovering their files and systems without paying the ransom.
If a system is powered off as files are being encrypted, some ransomware variants resume where they left off when the system or device is powered on again.
After files are encrypted, a ransom note is displayed on the screen with instructions on how and where to pay the ransom and the length of time before the hacker or software destroys the decryption key.
Some recent variants offer victims a ‘second chance’ to pay after the initial timer expires; however, the ‘second chance’ is often at least double the original ransom amount.
If the victim pays the ransom, the malware is supposed to contact the C2 server for the decryption key and begin decrypting the victim’s files; however, in many cases, the files are never decrypted.
Some ransomware files can delete themselves in order to avoid detection and analysis by security researchers or law enforcement.
CyberSecOP: Ransomware Remediation and Prevention Service
RANSOMWARE MITIGATION STRATEGIES
For many organizations, preventing ransomware entirely is nearly impossible, however, the impact of a successful infection can be greatly reduced if a robust data backup process is in place. Comprehensive data backups should be scheduled as often as possible and must be kept offline in a separate and secure location. The most effective method to prevent ransomware infections is to conduct regular training and awareness exercises with all employees to ensure users are proficient in safe Internet-browsing techniques and the ability to identify phishing emails. For specific recommendations for data protection, systems management, network management, mobile device management, and post-infection remediation.
5 steps for preventing ransomware
5 steps for preventing ransomware
Hardening Your Environment Against Ransomware
To avoid ransomware infection, follow these steps:
1. Back up your computers and servers regularly.
Regularly back up the files on both the client computers and servers. Either back up the files when the computers are offline or use a system that networked computers and servers cannot write to. If you do not have dedicated backup software, you can also copy the important files to removable media. Then eject and unplug the removable media; do not leave the removable media plugged in.
2. Lock down mapped network drives by securing them with a password and access control restrictions.
Use read-only access for files on network drives, unless it is absolutely necessary to have write access for these files. Restricting user permissions limits which files the threats can encrypt.
3. Deploy and enable the following Endpoint Protection:
Implement and managed endpoint antivirus on all endpoint to prevent ransomware, most ransomware can be detected by popular antivirus.
4. IPS/IDS
IPS blocks some threats that traditional virus definitions alone cannot stop. IPS is the best defense against drive-by downloads, which occurs when software is unintentionally downloaded from the Internet. Attackers often use exploit kits to deliver a web-based attack like CryptoLocker through a drive-by download.
See Enabling network intrusion prevention or browser intrusion prevention.
5. Download the latest patches for web application frameworks, web browsers, and web browser plug-ins.
Attacking exploit kits cannot deliver drive-by downloads unless there is an old version of a plug-in to exploit, such as Flash. Historically, attacks were delivered through phishing and web browsers. Recently, more attacks are delivered through vulnerable web applications, such as JBOSS, WordPress, and Joomla.
6. Use an email security product to handle email safely.
CryptoLocker is often spread through spam emails that contain malicious attachments. Scanning inbound emails for threats with a dedicated mail security product or service is critical to keep ransomware and other malware out of your organization. For important advice and recommendations, see:
How to remove ransomware
There is no ransomware removal tool or CryptoLocker removal tool. Instead, if your client computers do get infected with ransomware and your data is encrypted, follow these steps:
1. Do not pay the ransom.
If you pay the ransom:
· There is no guarantee that the attacker will supply a method to unlock your computer or decrypt your files.
· The attacker uses the ransom money to fund additional attacks against other users.
2. Isolate the infected computer before the ransomware can attack network drives to which it has access.
3. Update the virus definitions and scan the client computers.
New definitions are likely to detect and remediate the ransomware. Configure Endpoint Protection to automatically downloads virus definitions to the client, as long as the client is managed and connected to the Symantec Endpoint Protection Manager.
4. Restore damaged files from a known good backup.
No security Endpoint Protection cannot decrypt the files that ransom lockers have sabotaged.
Submit the malware to antivirus provider.
If you can identify the malicious email or executable, submit it to antivirus provider.