CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Beyond the Headlines: The True Cost of Cybercrime
The adoption of artificial intelligence (AI) technologies has hyper-accelerated the amount of data being generated. This growth will continue exponentially as newer platforms and tools are developed. As businesses turn to novel insurance models, which by definition are new and do not resemble what we have known or used previously to evaluate the risks related to retaining sensitive data in the current cybersecurity climate. Organizations need to understand their risk profile and the financial reality of the loss of access to their data.
it’s more important than ever to truly understand and plan for the threat landscape and the potential financial implications associated with cyber incidents, data exfiltration, and work stoppages.
The importance of data and an organization's capacity to appropriately protect it will be essential factors in assessing overall risk, influencing investors, insurability, and overall profitability.
COVID-19 Prompts Increased Ransomware Attacks Against SMBs Healthcare Providers
With the inception of the COVID-19 pandemic, malicious actors are increasingly targeting small hospitals and health centers with ransomware attacks. This is likely because these organizations are more likely to pay the ransom to recover data, as they weigh the perceived cost/benefit to strengthening their IT infrastructure security, or moving part or all of their IT operations to cloud-based solutions.
Cybercriminals tend to specifically target direct patient care facilities such as hospitals, healthcare centers, medical practices and health and wellness centers; although their efforts are certainly not confined to the above-referenced provider classes. The average ransomware demand is in the neighborhood of $60,000; however, simply paying the ransom in no way guarantees that the attacker will remit the decryption key; in fact, quite the opposite may occur; paying a ransom may encourage the attacker to maintain the leverage they enjoy over the target.
The ultimate consequences of ransomware attacks can and often are quite severe, ranging from continued involuntary exploitation of the attacker/victim relationship, to business closure. In some cases, class action lawsuits (dependent on the attack vector and information yield).
As more organizations move employees to work from home, remote staff make it increasingly difficult for IT teams to police computer systems and prevent cyber-attacks. Attackers now have far more access points and endpoints to probe or exploit, with little to no security oversight.
Here at CyberSecOp, we have formulated several countermeasures that healthcare employers should employ to minimize the risk of their networks being penetrated and secure their sensitive information.
Add data storage: After backing up data, the next step is to store data offline, on a different network, or a cloud-based environment.
Maintain a strong information encryption policy: Healthcare data must be encrypted at rest and transit with the highest standards available so that even if cybercriminals acquired it, they would not be able to read it.
Formulate and maintain an Incident Response Plan: Develop and test an incident response plan to help mitigate the impact of certain destructive malware attacks.
Track all data: Security personnel should closely monitor the company’s digital assets within the organization. This is of particular importance now as healthcare facilities’ attack surface expands and becomes more complex with some staff working remotely.
Establish and maintain firewalls: To harden networks and connected equipment, healthcare facilities with devices running open services should place them behind the latest application firewalls. They should also implement proper change management and firewall reviews to ensure proper documentation and optimization of these devices.
Follow the trends: Be aware of current ransomware threats, attack trends, and make sure those trends are socialized and communicated throughout the organization. Awareness is key.
What is Cybersecurity Risk Management
Cyber Risk Management is the next evolution in enterprise technology risk and security for organizations that increasingly rely on digital processes to run their business. Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such doors and locks to protect homes and autos, vaults to protect money and precious jewels, and police, fire and security to protect against other physical risks.
What is cybersecurity risk management?
Rather than doors, locks and vaults, IT departments rely on a combination of strategies, technologies and user education to protect an enterprise against cybersecurity attacks that can compromise systems, steal data and other valuable company information, and damage an enterprise’s reputation. As the volume and severity of cyber attacks grow, the need for cybersecurity risk management grows with it.
Cybersecurity risk management takes the idea of real world risk management and applies it to the cyber world. It involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to make sure your organization is adequately protected.
Setting up your risk management system
Before setting up a cybersecurity risk management system, the enterprise needs to determine what assets it needs to protect and place a priority on. As the National Institute of Standards and Technology (NIST) points out in its Framework for Improving Critical Infrastructure Cybersecurity, there is no one-size-fits all solution. Different organizations have different technology infrastructures and different potential risks. Some organizations such as financial services firms and healthcare organizations, have regulatory concerns in addition to business concerns that need to be addressed in a cybersecurity risk management system. Cybersecurity should follow a layered approach, with additional protections for the most important assets, such as corporate and customer data. Remember that reputational harm from a breach can do more damage than the breach itself.
Risk management with CyberSecOp
Identity Services
Identity services help companies manage the explosion of digital identities and access to critical resources, both internal and cloud-based. In this age of digital transformation, the spheres of the individual’s life―as a professional, consumer, and private citizen―are interlinked in a complex digital structure, like a piece of fabric. The growing ability to piece together a digital picture of a person’s life and identity carries both risk and opportunity.
Wherever an organization is on its journey, we can help them achieve efficiencies, reduce risk, and evolve to support the changing needs of the digital business. With 20 years of identity management experience across the major industries, we offer field-tested accelerators and methods that are scalable and adaptive to each client’s specific set of business requirements.
Data Protection
Data Protection services help implement capabilities and technologies to protect sensitive data. As infrastructure and applications become more virtualized and adaptive, new cybersecurity gaps can be created as fast as old ones have been addressed, making the prevention of data breaches more difficult than ever. By prioritizing preventative and detective defenses around highly sensitive data, security teams can help reduce data loss and risk when attackers get past network, application, and infrastructure controls.
Leveraging these principles and an understanding of each client’s risk profile, CyberSecOp helps organizations design, implement, and manage capabilities to help better protect sensitive information across the end-to-end data lifecycle, and at an organization’s last line of defense.Application Security
In the era of digital transformation, application portfolios are becoming exponentially more diverse—and support a growing community of users. As the application “surface area” expands, so does cyber risk. Amid the change, one thing remains constant: applications are the lifeline of the business—and need to be a front line of cyber defense. It’s an important time for organizations to reexamine their approaches to application security.
Improving application security requires technical attention to individual applications, but also a broad framework across the application portfolio—from custom-developed to commercial off-the-shelf (COTS) applications and whether managed on-premise, on a mobile platform, in the cloud, or in a hybrid environment. It also requires the flexibility to support varying and often coexisting system methodology processes from waterfall, to agile, to DevOps in order to address application-related cyber risk at the pace of the organization’s digital evolution.
CyberSecOp’s application security services help organizations to design and implement security mechanisms across the system development methodology that can flex to your operational requirements to drive value through IT while also protecting your application portfolio against the changing cyber threat landscape.Infrastructure Security
Infrastructure Security services focus on developing advanced protection of core systems and devices. Today’s critical business drivers—the need to digitally transform, modernize the supply chain, enhance customer experience, increase agility, reduce costs, etc.—are driving a major shift in technology priorities. This shift includes increasing focus on cloud adoption, the Internet of Things (IoT), hybrid computing, software-defined networks (SDN), robotic process automation (RPA), blockchain, artificial intelligence, and more. The infrastructure supporting it has become highly virtualized and automated—and the traditional means of securing infrastructure fall short.
CyberSecOp helps organizations move toward a modernized, risk-focused agile defense approach. While the basic infrastructure domains—physical facilities, networks, systems and storage, and endpoints—that need to be protected remain the same, the means to secure them must evolve. By providing assessment, strategy, architecture, implementation, and operational management assistance across the four infrastructure domains, we help clients face our brave new world with a transformed, agile defense capability.
Cyber Insurance - Is a must have - you will need it
Cyber Insurance - Is a must have - you will need it.
It’s every healthcare organization’s nightmare to get the call that their data has been breached or hacked. As a result, many have turned to cyber insurance to protect assets and business operations.
As cyber policies and carriers lack a universal policy, there’s an even greater worst case scenario: An organization is breached, and the policy doesn’t cover what the leaders thought it did. Now, not only is the healthcare provider strapped with the burden of the breach, it wasted money on a useless cyber insurance policy.
To get a better grasp on how to choose the right policy, Healthcare IT News asked attorney Matthew Fisher, partner with Mirick O’Connell, and Jane Harper, Henry Ford Health System’s director of privacy and security risk management, to outline the biggest policy mistakes -- and how to avoid them.
Mistake #1: Rushing the process
When buying a policy, a carrier will provide a questionnaire that will evaluate your organization’s security posture, program, tools and policies. The biggest mistake is to rush the pre-policy process to see the rates and what the carrier will cover, explained Fisher.
Organizations need to be conservative with how they answer the questions, as “it could be a ground for denial, if you don’t have the policies you said you have in place,” said Fisher. “You have to make sure you’re not unintentionally misleading the insurance company when it comes to coverage.”
Often these questionnaires attempt to create a black and white policy and “it can be tough to answer correctly,” explained Fisher.
“Your ability to be as transparent and truthful upfront is critical to the nonpayment discussion,” said Harper. “If you tell the insurance company that you have everything in place and are compliant, if you tell them that and then you have an issue, and you weren’t truthful, it ends up being a legal battle.”
“When you submit your checklist that they have you fill out, meet with the underwriter to make sure you understand what you’ve documented,” she added. “You also need the copy that was provided to the insurance company because it will come back into play when you submit the final documents.”
For example, if you say you have a specific control in place, and you actually don’t, Harper explained that can create a situation where “they thought they had an understanding of something, but they didn’t.”
“Be honest, transparent and accurate -- because they can deny your policy if you were inaccurate or misleading in your responses,” she said.
Mistake #2: Lax, incomplete risk assessment
It’s easier to prevent a misleading or false statement to an underwriter, when an organization has a strong assessment and inventory of the processes and tools on the system. But far too often, hospitals “don’t know everything about the control environment,” explained Harper.
“When you talk about protecting an system and preventing a cyber incident, you have to have a good understanding of the organization’s overall control environment,” Harper said. “It’s key, as the longer it takes you to identify that you’ve had an incident, it leads to more exposure and the longer it takes to recover.”
But it’s also important to remember to update this inventory or assessment when buying new tools, merging with other organizations, hiring new staff and the like, Harper explained.
“Think about all of the activities and operations that happen,” she said. “And every three years, you’re updating a cybersecurity checklist -- that may not be frequent enough.”
For example, Harper explained that an organization filling out the policy questionnaire may have all of the right elements in place. But if another tool was purchased and the controls weren’t updated or the control was removed and the underwriter was not notified, there could be a problem.
“If those controls played into how the underwriter rated you: that can be key,” said Harper. “Think about your own home: you get additional discounts when you have a burglar alarm. So if you get one, and let them know, you may get a lower rate… But if you no longer have that control, you have to tell the carrier.”
“It’s the same kind of practice that we want to get into when we get into cyber insurance for our organization,” she added.
Mistake #3: Failing to involve the right people
Many organizations understand that security needs to exist outside of the IT team. In the same vein, it’s crucial when buying a cyber insurance policy that the same mentality is applied to make sure all of your bases are covered.
“Make sure you are talking to the right individuals,” Harper said. “The appropriate key stakeholders are not only involved with the evaluation process - how many patients, how much data, etc. -- but also the responses to the questions the policy is going to ask.”
“Risk folks typically talk about it as it relates to patients,” she continued. “Those folks are key, but in addition, you need your privacy and security risk professionals, security officers, IT leader, your key business leaders/owners and those driving the data. It’s key.”
Also crucial? Making sure the facilities team is involved, as there can sometimes be a cyber incident based on a physical issue. Harper explained that “often people tend to focus on things like electronic PHI, but there’s physical PHI. If there’s a break in at a warehouse and data is stolen, OCR considers that a breach.”
Mistake #4: Failing to understand coverage
Far too often organizations make large assumptions as to just what cyber insurance will cover. Fisher explained that these leaders are often shocked to learn that they did not receive the full spectrum of coverage they wanted.
“Relying on blind faith on those terms, or what the broker or agent is telling you is a major mistake,” said Fisher. “It’s always up to up to you to go into something with eyes fully wide open to make sure you know what you’re actually buying.”
Harper took it a step further and laid to rest a common misconception when it comes to coverage: “Insurance will not cover fines and penalties associated with noncompliance. If you’re not complaint, and you didn’t do risk assessments, cyber insurance won’t protect you from that, so don’t expect it.”
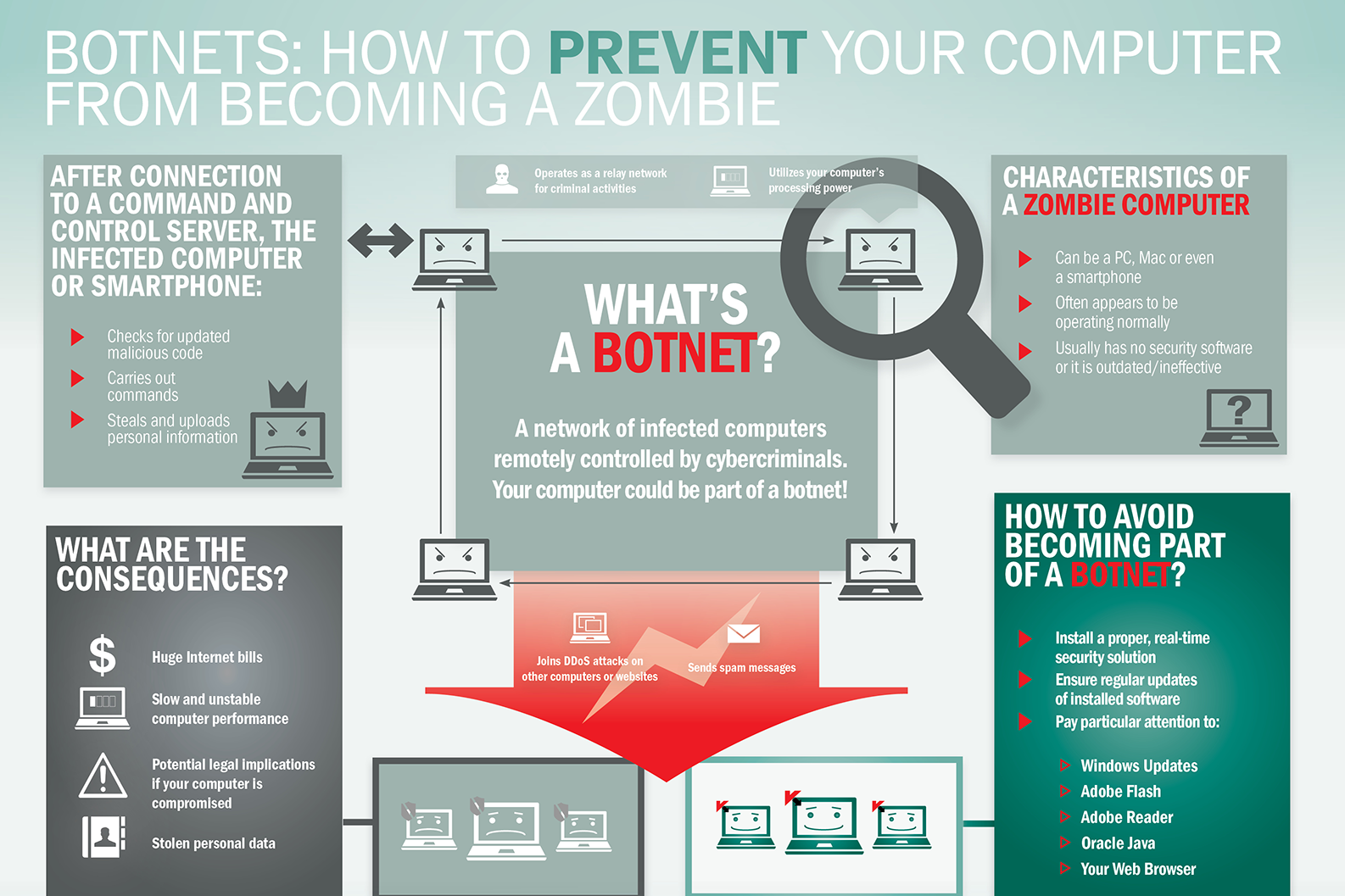
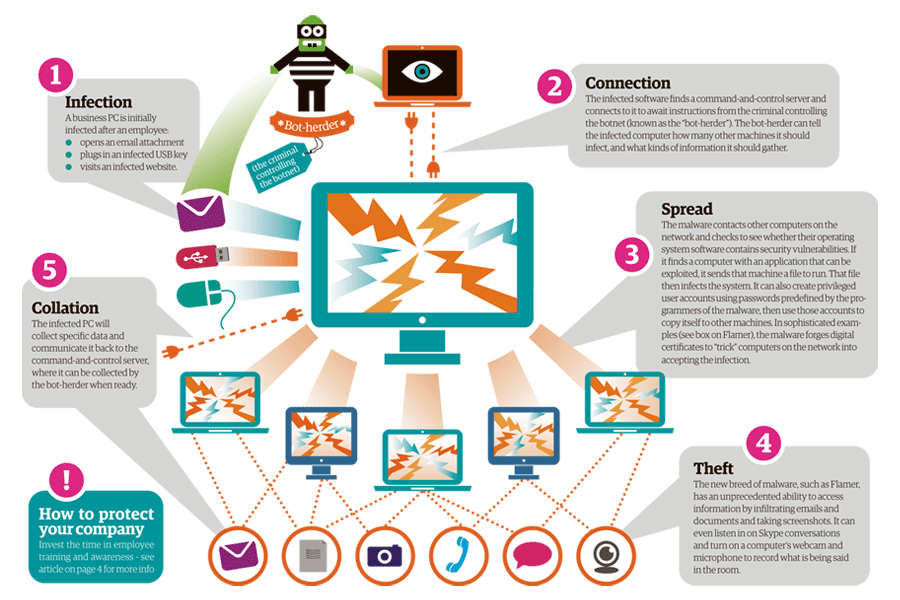
What is Botnet - Cybercriminals #1 Weapon
The word Botnet is formed from the words ‘robot’ and ‘network’. Cybercriminals use special Trojan viruses to breach the security of several users’ computers, take control of each computer and organise all of the infected machines into a network of ‘bots’ that the criminal can remotely manage.
Botnet Prevention- What is Botnet
How Botnets can impact you
Often, the cybercriminal will seek to infect and control thousands, tens of thousands or even millions of computers – so that the cybercriminal can act as the master of a large ‘zombie network’ – or ‘bot-network’ – that is capable of delivering a Distributed Denial of Service (DDoS) attack, a large-scale spam campaign or other types of cyberattack.
In some cases, cybercriminals will establish a large network of zombie machines and then sell access to the zombie network to other criminals – either on a rental basis or as an outright sale. Spammers may rent or buy a network in order to operate a large-scale spam campaign.
How to prevent your computer becoming part of a Botnet
Installing effective anti-malware software will help to protect your computer against Trojans and other threats.
Secure Google Chrome from Hacking Attacks
Google Chrome is definitely one of the most popular web browsers being used today. Hackers, as we know, are perpetually after whatever gets popular in the world of the internet. This because whatever is popular would help them target more people and steal more data. Thus, Google Chrome too happens to be among the most favorite for cyber criminals across the world. Hence, securing Google Chrome against hacking attacks is really important.
So, how do we secure Google Chrome from cyber attacks? Well, it’s a multi-step process. Lots of things have to be done. Securing your browser is important as it helps secure your device, your internet connection and more importantly, your personal and business data.
Let’s discuss, in detail, what all needs to be done to secure Google Chrome from hacking attacks. Here we go:
Begin by ensuring that your Google account is properly secured!
This is something basic, your Google account needs to be properly secured. Chrome lets you sign in from any device, anytime. Hence, it’s important to ensure the security of your Google account. You need to make sure you are logged out of your account every time you sign in, on any device. You also need to ensure that your password is secure. If you aren’t signed out or if someone knows/cracks your password, it would be easy to manipulate things and cause you harm. Your data could be stolen.
Keeping the browser secured is equally important…
Keeping the browser secured is as important as securing your Google account. You could use a password to protect your browser, and thus, in your absence, no one would be able to take control of your browser and do mischiefs. Similarly, every time you leave your terminal, it’s good to go out of the browser as well.
Keep your browser ‘clean’!
You should make it a habit to keep your browser ‘clean’, by wiping out most of the information from it. In fact, there should be some plan/schedule as regards cleaning the browser. Clear the history periodically, either everytime you log out or at least once every week if not once a day.
Never save passwords on the browser
The browser might offer to ‘remember’ your passwords for you so that you could sign in easily the next time you’re using some service. But it’s always good not to save passwords on the browser. If you save your passwords, it would be possible for someone else to get into your account and misuse it or steal information.
Having a master password helps
Having a master password, which would help you get to your other saved passwords in Chrome, is a good thing to do. Thus you need not worry about remembering all of your passwords and you don’t have to be afraid of your passwords getting stolen or misused either.
Keep your device protected
The device that you use to browse needs to be protected from malware and hacking. For this, you must use whatever security tools you need and also have alerts that tell you if at all your device is compromised. Remember a compromised device means an unsecured browser!
Keep the device locked whenever you’re not using it
Always keep your device locked when you are not using it, be it a computer or any other mobile device. That prevents people from getting on to your device and hijacking your browser and your data as well. Locking your device also gets it off the WiFi network that you are using.
Secure your network, never use unsafe WiFi networks
Securing your network is important; it helps a lot in securing Google Chrome from hacking attacks. Hence you need to do all that is needed to secure your network. Similarly, it’s always advisable never to use unsafe WiFi networks. Whenever you’re using a WiFi network, ensure it’s properly encrypted and if possible use an app or program that would prevent hacking. In fact, using a secure network secures not just your browser, but everything on your device/system.
Trust Chrome for phishing detection
Google Chrome does its own phishing detection and protects you from many phishing websites. So, when your browser tells you that a website is not safe, it’s always advisable to trust it and avoid such sites.
Avoid phishing websites and attachments yourself
In addition to Google Chrome detecting phishing websites for you, it’s always good that you yourself stay away from websites/attachments that could be used for phishing scams. Staying away from such suspicious websites secures your browser, your system/network and your data.
Small Business Benefits from Cybersecurity Consulting Services
Cybersecurity news stories are becoming more and more prevalent, especially over the last few years. Whether the stories are about stolen emails or huge data breaches, it has been virtually impossible to ignore them.
While the major stories about compromised corporations and hacked email accounts make the news, cybersecurity is something that concerns everyone who uses a computer. Even small business owners can become victims of cybercrime. In fact, small business owners, in particular, need to be concerned with cybersecurity so they can protect their intellectual property. No matter whether the intellectual property is research or recipes, it is one of the greatest assets a small business has. Intellectual property is a prime target for hackers, whether they are stealing information for a competitor or running a ransomware scheme where a hacker demands something in return for the stolen information.
The trouble is that protecting that intellectual property and keeping other sensitive information, such as client and customer data, isn’t cheap. Many small business owners may not have the available capital to afford a cybersecurity system. Although this puts an owner in a tough spot, you can’t put a price on peace of mind, and neither can a small business owner afford the losses associated with becoming the victim of a cybercrime.
As with most things for small-business owners, cybersecurity comes down to a cost analysis. A cybersecurity system can be a big expense. On the other hand, a small business owner has to consider the cost of not having their systems protected from hackers. It’s hard enough for a large corporation to recover from a cyber attack, even with all the resources and infrastructure they have. According to the U.S. National Cyber Security Alliance, 60 percent of small businesses fold within six months of a cyber attack.
Ultimately, each business owner has to decide if and when a formal data security protection plan is necessary. A consultation with an expert may help you better weigh the pros and cons of taking on this type of business expense. Start with this list of Cybersecurity Consulting Providers as a jumping off point for your research. After comparing the benefits of these companies’ plans, set up a few consultations to see if and how these providers can best help protect your business, and what it costs to do so. You may find that it’s worth the investment.